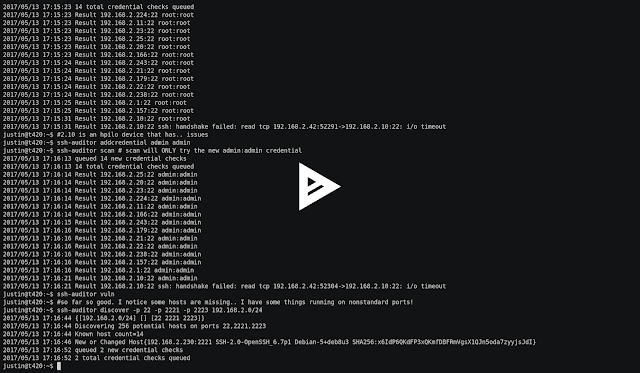
The Best Way To Scan For Weak Ssh Passwords On Your Network Features ssh-auditor will automatically: Re-check all known hosts as new credentials are added. It...
Search Results For - Discover
Manticore is a symbolic execution tool for analysis of binaries and smart contracts. Note: Beginning with version 0.2.0, Python 3.6+ is required. Features...
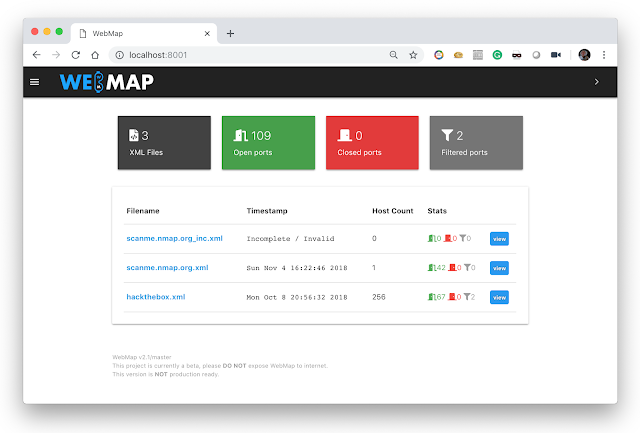
A Web Dashbord for Nmap XML Report Usage You should use this with docker, just by sending this command: $ mkdir /tmp/webmap $ docker run -d --name webmap -h...
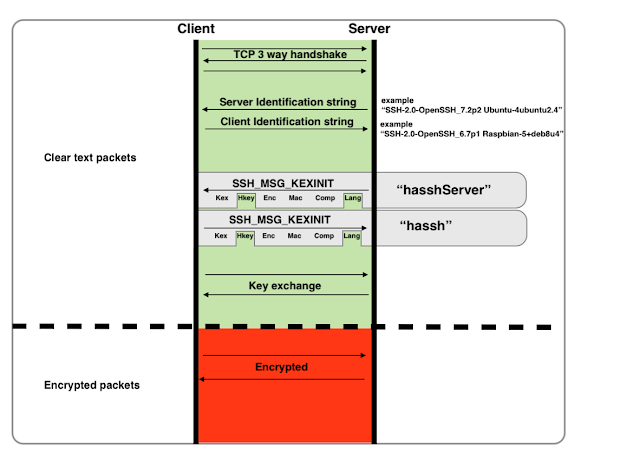
“HASSH” is a network fingerprinting standard which can be used to identify specific Client and Server SSH implementations. The fingerprints can be...
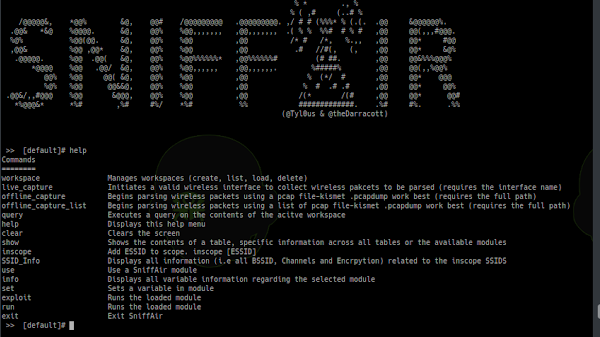
SniffAir is an open-source wireless security framework which provides the ability to easily parse passively collected wireless data as well as launch...
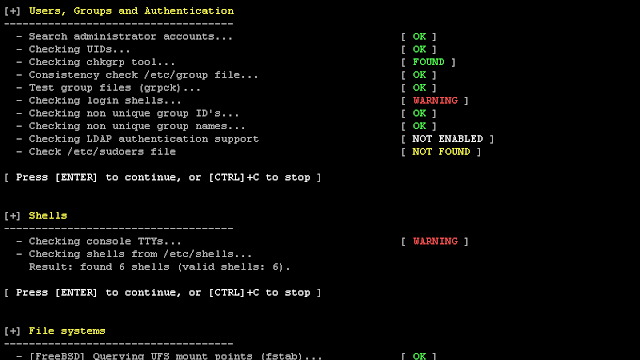
We are excited to announce this major release of auditing tool Lynis. Several big changes have been made to core functions of Lynis. These changes are the next...
Welcome to our fourth and final release of 2018, Kali Linux 2018.4, which is available for immediate download. This release brings kernel up to version 4.18...
Tumblr today published a report admitting the presence of a security vulnerability in its website that could have allowed hackers to steal login credentials...
A 21-year-old Kentucky man who previously pleaded guilty to developing, marketing, and selling an infamous remote access trojan (RAT) called LuminosityLink has...
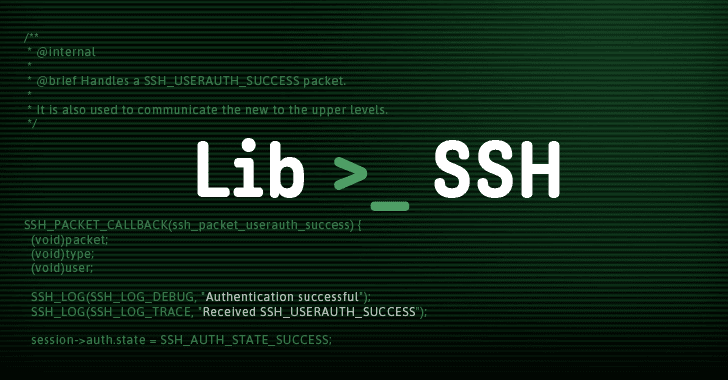
A four-year-old severe vulnerability has been discovered in the Secure Shell (SSH) implementation library known as Libssh that could allow anyone to completely...