[sc name=”ad_1″] At NDSS Symposium 2019, a group of university researchers yesterday revealed newly discovered cellular network vulnerabilities...
Search Results For - Discover
[sc name=”ad_1″] A team of cybersecurity researchers from the University of New Haven yesterday released a video demonstrating how vulnerabilities...
[sc name=”ad_1″] Beware Windows users… a new dangerous remote code execution vulnerability has been discovered in the WinRAR software...
[sc name=”ad_1″] Exclusive — If you have not updated your website to the latest WordPress version 5.0.3, it’s a brilliant idea to upgrade the...
[sc name=”ad_1″] A low interaction honeypot with the capability to be more of a medium interaction honeypot. HoneyPy is written in Python2 and is...
[sc name=”ad_1″] Why would someone bother to hack a so-called “ultra-secure encrypted database that is being protected behind 13 feet high...
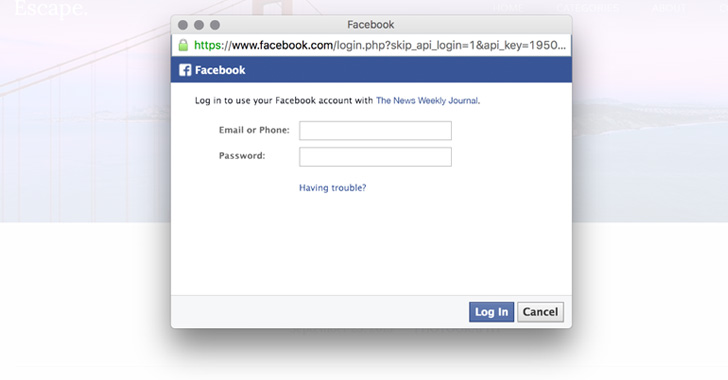
[sc name=”ad_1″] It’s 2019, and just clicking on a specially crafted URL would have allowed an attacker to hack your Facebook account without...
[sc name=”ad_1″] It’s not at all surprising that downloading movies and software from the torrent network could infect your computer with...
[sc name=”ad_1″] How do you check if a website asking for your credentials is fake or legit to log in? By checking if the URL is correct? By...
[sc name=”ad_1″] A serious security vulnerability has been discovered in the core runC container code that affects several open-source container...