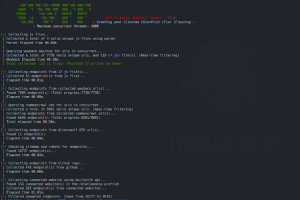
[sc name=”ad_1″] Tested environments: Windows, MAC, linux, and windows subsystem for linux (WSL) What can SourceWolf do? Crawl through responses to...
Search Results For - Discover Subdomains
[sc name=”ad_1″] CWFF is a tool that creates a special High quality fuzzing/content discovery wordlist for you at the highest speed possible using...
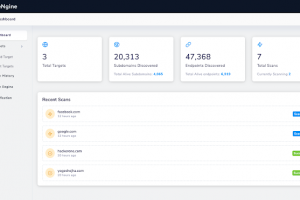
[sc name=”ad_1″] reNgine is an automated reconnaissance framework meant for gathering information during penetration testing of web applications...
[sc name=”ad_1″] Docker for pentest is an image with the more used tools to create an pentest environment easily and quickly. Features OS...
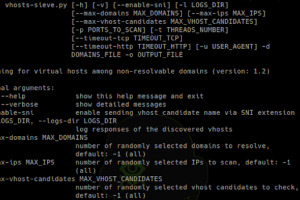
[sc name=”ad_1″] Searching for virtual hosts among non-resolvable domains. Installation git clone pip3 install -r vhosts-sieve/requirements.txt...
[sc name=”ad_1″] A collection of cool tools used by Web hackers. Happy hacking , Happy bug-hunting. Weapons Type Name Description Popularity...
[sc name=”ad_1″] A list of useful payloads and bypasses for Web Application Security. Feel free to improve with your payloads and techniques ...
[sc name=”ad_1″] Lockdoor Framework : A Penetration Testing Framework With Cyber Security Resources. 09/2019 : 1.0Beta Information Gathring Tools...
[sc name=”ad_1″] Introduction Dr. ROBOT is a tool for Domain Reconnaissance and Enumeration. By utilizing containers to reduce the overhead of...
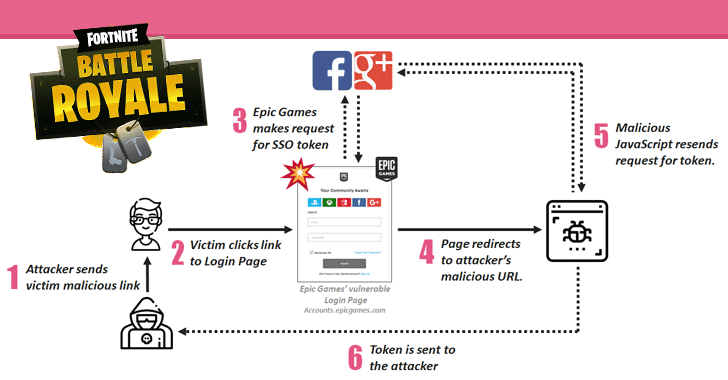
[sc name=”ad_1″] Check Point researchers have discovered multiple security vulnerabilities in Fortnite, a massively popular online battle game, one...