[sc name=”ad_1″] GitMonitor is a Github scanning system to look for leaked sensitive information based on rules. I know that there are a lot of...
Search Results For - Diagram
[sc name=”ad_1″] A collection of cool tools used by Web hackers. Happy hacking , Happy bug-hunting. Weapons Type Name Description Popularity...
[sc name=”ad_1″] A Undetectable Payload Generation. This tool is for educational purpose only, usage of Kaiten for attacking targets without prior...
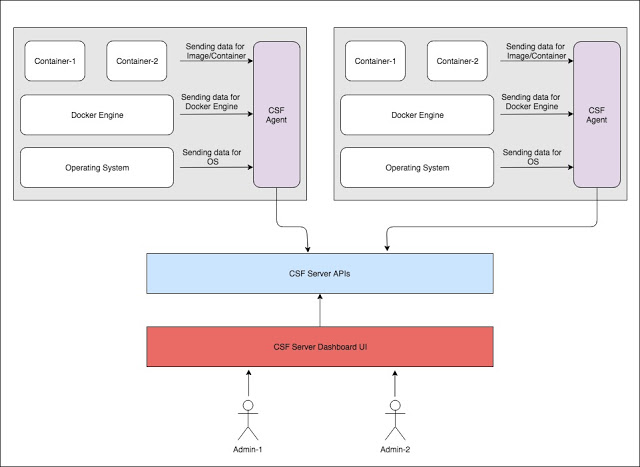
[sc name=”ad_1″] ArmourBird CSF – Container Security Framework is an extensible, modular, API-first framework build for regular security...
[sc name=”ad_1″] It is utmost important for any security engineer to understand their network first before securing it and it becomes a daunting...
[sc name=”ad_1″] If you are a Counter-Strike gamer, then beware, because 39% of all existing Counter-Strike 1.6 game servers available online are...
Security Monkey monitors your AWS and GCP accounts for policy changes and alerts on insecure configurations. Support is available for OpenStack public and...
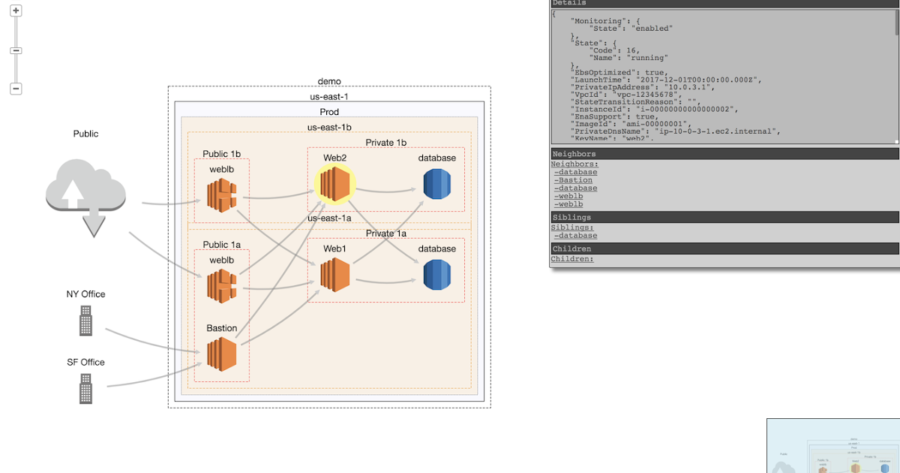
CloudMapper helps you analyze your Amazon Web Services (AWS) environments. The original purpose was to generate network diagrams and display them in your...
Author: Colin Harper If you’ve ever dealt in Bitcoin, you may have suffered through hour-long (or at worst, day-long) transaction times. It’s becoming...