[sc name=”ad_1″] A serious security vulnerability has been discovered in the core runC container code that affects several open-source container...
Search Results For - Debian
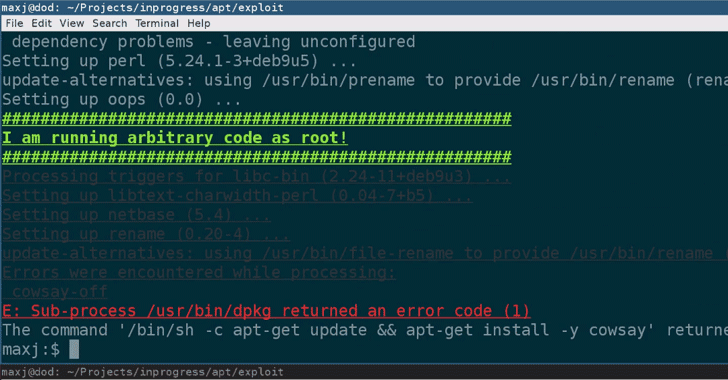
[sc name=”ad_1″] Ubuntu and some other Linux distributions suffer from a severe privilege escalation vulnerability that could allow a local...
[sc name=”ad_1″] Just in time… Cybersecurity experts this week fighting over Twitter in favor of not using HTTPS and suggesting software developers...
[sc name=”ad_1″] Security researchers have discovered three vulnerabilities in Systemd, a popular init system and service manager for most Linux...
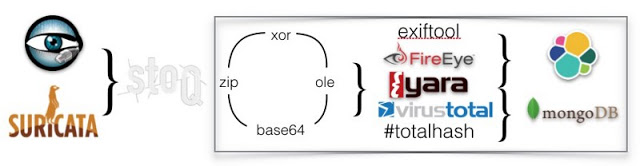
[sc name=”ad_1″] stoQ is a automation framework that helps to simplify the more mundane and repetitive tasks an analyst is required to do. It...
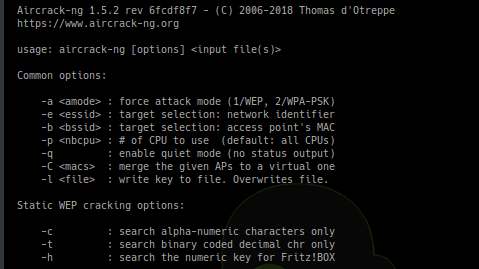
[sc name=”ad_1″] Aircrack-ng is a complete suite of tools to assess WiFi network security. It focuses on different areas of WiFi security:...
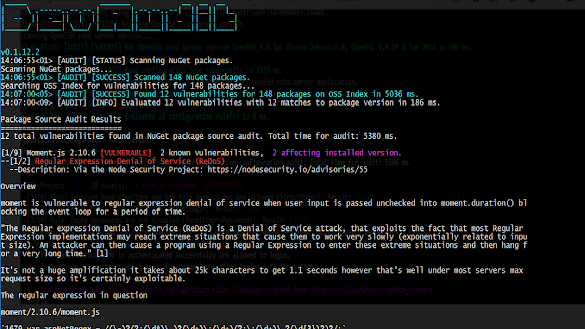
[sc name=”ad_1″] DevAudit is an open-source, cross-platform, multi-purpose security auditing tool targeted at developers and teams adopting DevOps...
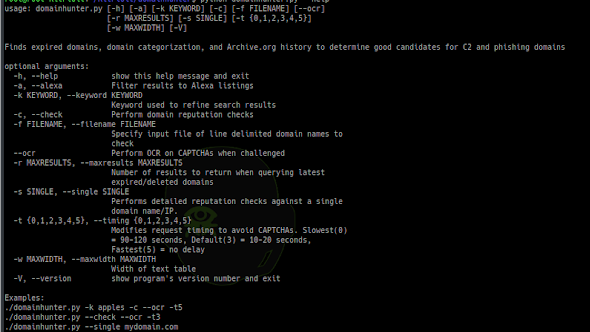
Domain name selection is an important aspect of preparation for penetration tests and especially Red Team engagements. Commonly, domains that were used...
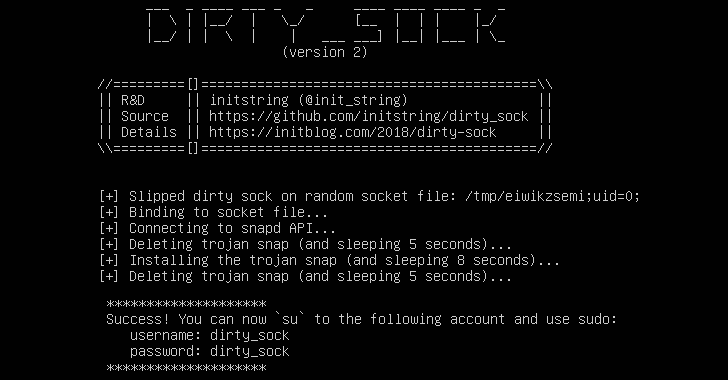
[sc name=”ad_1″] Hold tight, this may blow your mind… A low-privileged user account on most Linux operating systems with UID value anything greater...
Tested on Kali Linux. Should work with all Debian based distros (and other ones if you have the right packages installed) BabySploit is a penetration testing...