[sc name=”ad_1″] Hardened Debian GNU/Linux and CentOS 8 distro auditing. The main test environment is in debian GNU/Linux 9/10 and CentOS 8, and...
Search Results For - Debian
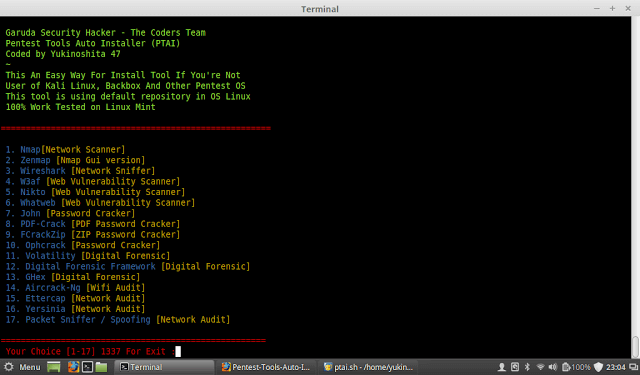
A Simple tool for installing pentest tools and forensic tools on Debian / Ubuntu Based OS Tested on Linux Mint And Kali Linux How To Do ?? Change Your...
[sc name=”ad_1″] A Hex Editor for Reverse Engineers, Programmers and people that value their eye sight when working at 3 AM. Features Featureful...
[sc name=”ad_1″] Automated Web Assets Enumeration & Scanning Instructions for running Create an account on Zulip Navigate to...
[sc name=”ad_1″] Sploit is a Go package that aids in binary analysis and exploitation. The motivating factor behind the development of sploit is to...
[sc name=”ad_1″] Stegseek is a lightning fast steghide cracker that can be used to extract hidden data from files. It is built as a fork of the...
[sc name=”ad_1″] enum4linux-ng.py is a rewrite of Mark Lowe’s (former Portcullis Labs now Cisco CX Security Labs) enum4linux.pl, a tool for...
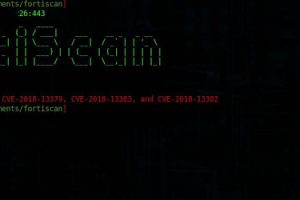
[sc name=”ad_1″] (CVE-2018-13379) Exploitation Tool, You can use this tool to check the vulnerability in your FortiGate SSL-VPN. ...
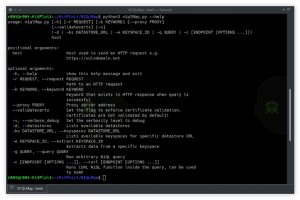
[sc name=”ad_1″] N1QLMap is an N1QL exploitation tool. Currently works with Couchbase database. The tool supports data extraction and performing...
[sc name=”ad_1″] ToothPicker is an in-process, coverage-guided fuzzer for iOS. It was developed to specifically targets iOS’s Bluetooth...