Cybercriminals decided to use the Search Engine Optimization (SEO) to make their malicious links more widespread in the search results, allowing them to gain...
Search Results For - Cyber
In 2013, Hackers apparently gained access to the Trump Organization’s domain booking account and created at least 250 website subdomains that cybersecurity...
The CryptoShuffler malware has been discovered by security researchers from Kaspersky Lab, cybercriminals are using this malware to steal cryptocurrencies from...
FireEye’s Innovation and Custom Engineering (ICE) team released a tool called GoCrack that allows red teams to efficiently manage password cracking tasks...
“I don’t remember if my data has been sold to the dark web or where this goes,” she said. “I keep getting letters from Kohl’s, from Macy’s, from Old Navy...
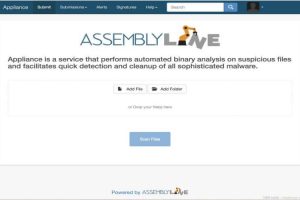
Assemblyline is a scalable distributed file analysis framework. It is designed to process millions of files per day but can also be installed on a single box...
Qubes OS is a security-oriented operating system (OS). The OS is the software that runs all the other programs on a computer. Some examples of popular OSes are...
News reported in June that McAfee was amongst several Western technology organizations that had acceded in recent years to larger demands by Moscow for access...
In response to law enforcement’s increased involvement with targeting the illegal activities taking place on the Dark Web, criminals have began to use...
The British government has admitted publicly for the first time that it is all but certain North Korea carried out the “WannaCry” malware attack...