[sc name=”ad_1″] Security researchers have discovered two high-severity vulnerabilities in the SHAREit Android app that could allow attackers to...
Search Results For - Cross Platform
[sc name=”ad_1″] A team of cybersecurity researchers from the University of New Haven yesterday released a video demonstrating how vulnerabilities...
[sc name=”ad_1″] How do you know whether an attacker has infiltrated your network? Can you really rely on an Endpoint Detection and Response (EDR)...
[sc name=”ad_1″] It’s 2019, and just clicking on a specially crafted URL would have allowed an attacker to hack your Facebook account without...
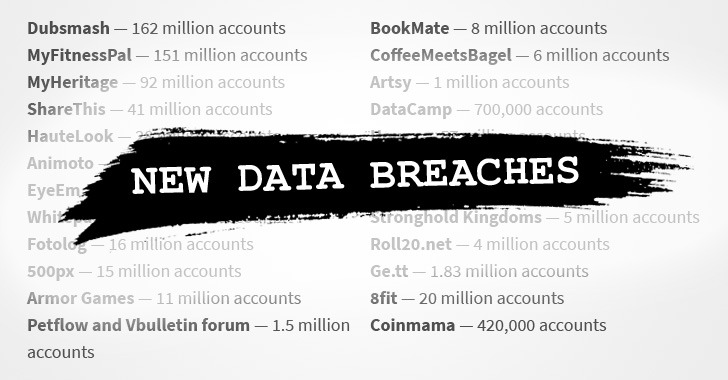
[sc name=”ad_1″] A hacker who was selling details of nearly 620 million online accounts stolen from 16 popular websites has now put up a second...
[sc name=”ad_1″] Welcome back! Adobe has today released its monthly security updates to address a total of 75 security vulnerabilities across its...
[sc name=”ad_1″] A malicious Windows EXE file can even infect your Mac computer as well. Yes, you heard me right — a .exe malware on macOS...
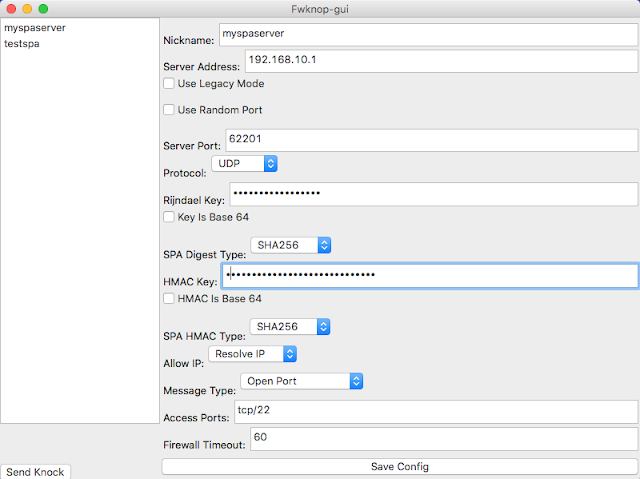
[sc name=”ad_1″] fwknop implements an authorization scheme known as Single Packet Authorization (SPA) for strong service concealment. SPA requires...
[sc name=”ad_1″] A security researcher has discovered multiple one-click client-side vulnerabilities in the some of the world’s most popular...
[sc name=”ad_1″] If you are responsible for the cybersecurity of a medium-sized company, you may assume your organization is too small to be...