A four-year-old severe vulnerability has been discovered in the Secure Shell (SSH) implementation library known as Libssh that could allow anyone to completely...
Search Results For - Control
A dark web drugs kingpin who was arrested last year when he arrived in the United States to compete in the World Beard and Mustache Championships has now been...
Yes, it is official. The massively popular battle royale video game from Epic Games, Fortnite: Battle Royale is finally available for Android devices. Epic...
A security researcher has discovered several critical vulnerabilities in one of the most popular embedded real-time operating systems—called FreeRTOS—and its...
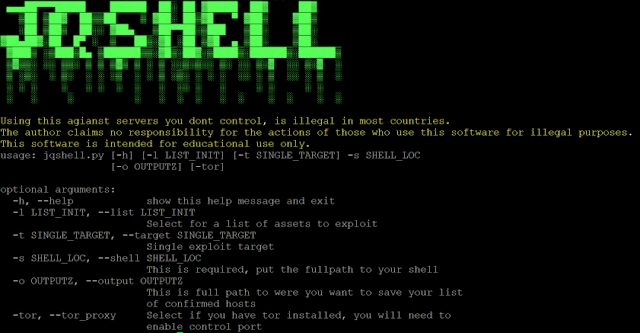
JQShell A weaponized version of CVE-2018-9206 (Unauthenticated arbitrary file upload vulnerability in Blueimp jQuery-File-Upload <= v9.22.0). Disclaimer...
Microsoft Windows built-in anti-malware tool, Windows Defender, has become the very first antivirus software to have the ability to run inside a sandbox...
Nubia is a lightweight framework for building command-line applications with Python. It was originally designed for the “logdevice interactive shell (aka...
Cybersecurity firm FireEye claims to have discovered evidence that proves the involvement of a Russian-owned research institute in the development of the...
AutoRDPwn is a script created in Powershell and designed to automate the Shadow attack on Microsoft Windows computers. This vulnerability allows a remote...
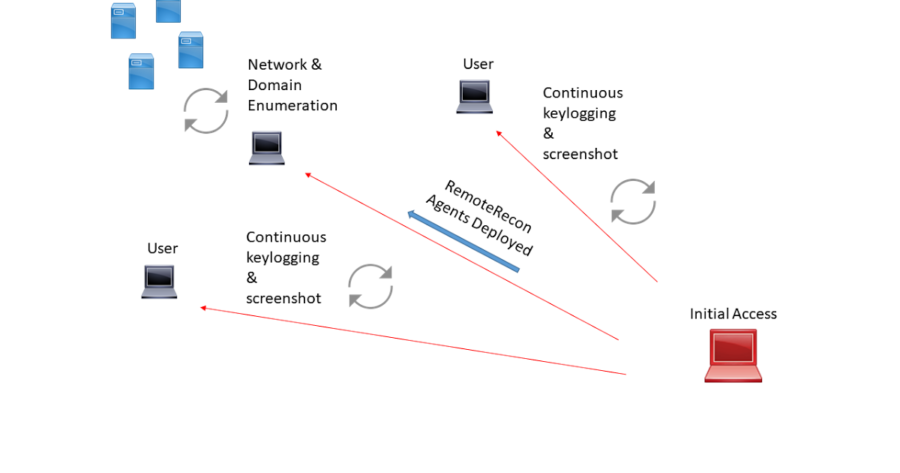
RemoteRecon provides the ability to execute post-exploitation capabilities against a remote host, without having to expose your complete toolkit/agent. Often...