This small script will simulate fake processes of analysis, sandbox and/or VM software that some malware will try to avoid. You can download the original...
Search Results For - Code Analysis
A pattern based Dalvik deobfuscator which uses limited execution to improve semantic analysis. Also, the inspiration for another Android deobfuscator: Simplify...
Taking advantage of Intel ME technology, within which attackers can execute unsigned code on the target machine. This leads to a full compromise of the...
Seccubus automates regular vulnerability scans with various tools and aids security people in the fast analysis of its output, both on the first scan and on...
The Port Scan Attack Detector psad is a lightweight system daemon written in is designed to work with Linux iptables/ip6tables/firewalld firewalling code to...
[sc name=”ad_1″] JavaScript AST analysis. This package has been created to export the Node-Secure AST Analysis to enable better code evolution and...
[sc name=”ad_1″] A curated list of Android Security materials and resources For Pentesters and Bug Hunters. Blog AAPG – Android application...
[sc name=”ad_1″] flare-emu marries IDA Pro’s binary analysis capabilities with Unicorn’s emulation framework to provide the user with an easy to...
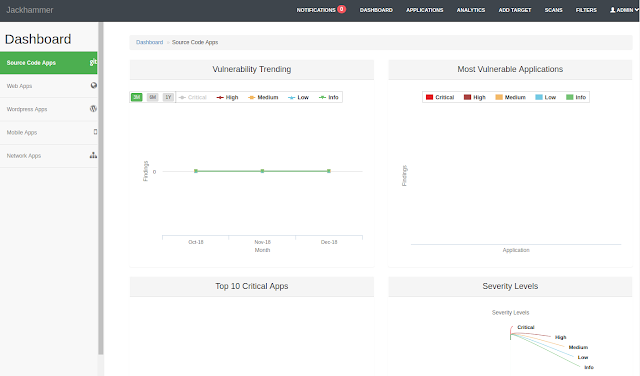
[sc name=”ad_1″] One Security vulnerability assessment/management tool to solve all the security team problems. What is Jackhammer? Jackhammer is a...
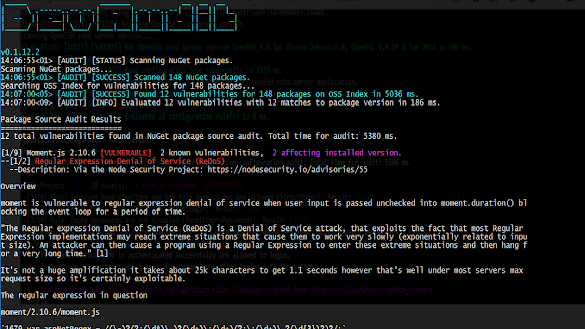
[sc name=”ad_1″] DevAudit is an open-source, cross-platform, multi-purpose security auditing tool targeted at developers and teams adopting DevOps...