Across the Internet, hundreds of thousands of sites rely on Google’s reCaptcha system for defense against bots (in fact, Devpost uses reCaptcha when creating a...
Search Results For - Cloud
Exitmap is a fast and modular Python-based scanner for Tor exit relays. Exitmap modules implement tasks that are run over (a subset of) all exit relays. If you...
Paskto will passively scan the web using the Common Crawl internet index either by downloading the indexes on request or parsing data from your local system...
LG has updated its software after security researchers spotted a flaw that allowed them to gain control of devices like refrigerators, ovens, dishwashers, and...
The official blog of jQuery—most popular JavaScript library used by millions of websites—has been hacked by some unknown hackers, using the pseudonym...
An unknown hacker has hijacked Coinhive’s DNS server and modified the legitimate Coinhive JavaScript in-browser miner with a malicious one that mined Monero...
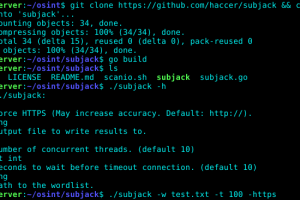
subjack is a Hostile Subdomain Takeover tool written in Go designed to scan a list of subdomains concurrently and identify ones that are able to be hijacked...
Shadow is a unique discrete-event network simulator that runs real applications like Tor and Bitcoin, and distributed systems of thousands of nodes on a single...
Google lists just over 1,300 people on its research website, not all of whom specialize in AI. It has many thousands more software engineers. Google parent...
Smart Home Systems like the Google Home Mini is intended to only listen for a specific wake word, in this case, it’s “Hey Google” or “Ok Google.” Only then do...