Interview: Aragon’s Luis Cuende on Blockchain Governance & Digital Jurisdictions Author: Bennett Garner Bennett Garner: You’ve said “humans enforce...
Search Results For - Cloud
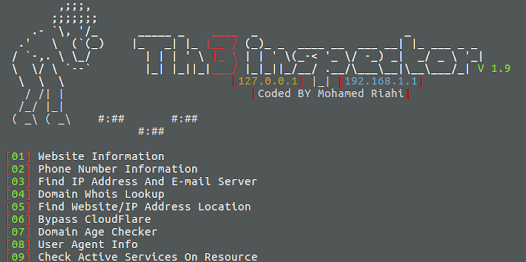
Tool For Information Gathering. Usage Short Form Long Form Description -i –info Website Information -n –number Phone Number Information -mx...
Tool to check if a given IP is a node tor or an open proxy. Why? Sometimes all your throttles are not enough to stop brute force attacks or any kind of massive...
The prosecutions were filed in California, Oregon, and Indiana, according to The News. The three incidents focus on the setback in Intel disclosing the...
Defeating Google’s audio reCaptcha system with 85% accuracy. Inspiration Across the Internet, hundreds of thousands of sites rely on Google’s...
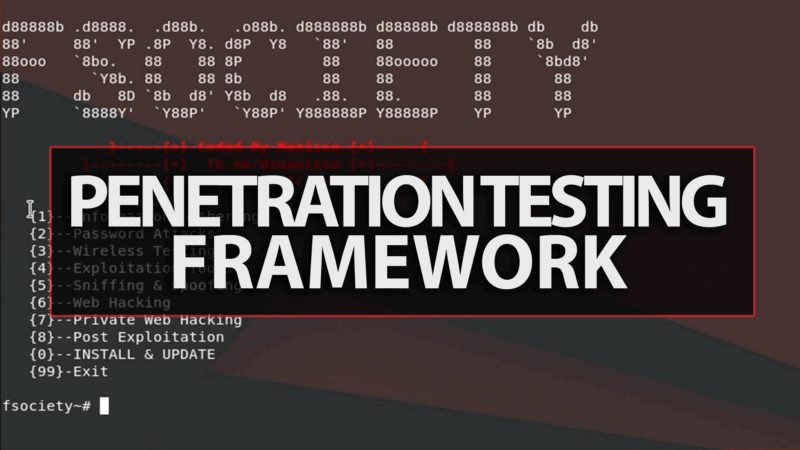
A Penetration Testing Framework, you will have every script that a hacker needs Fsociety: Menu Information Gathering Password Attacks Wireless Testing...
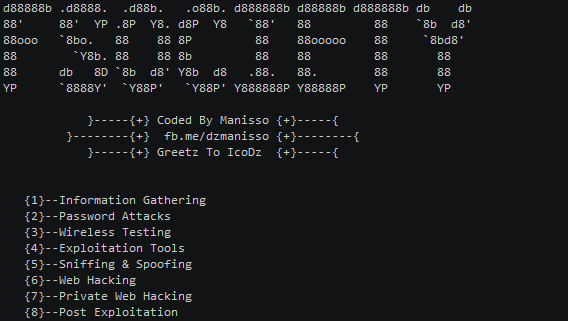
A Penetration Testing Framework , you will have every script that a hacker needs Menu Information Gathering Password Attacks Wireless Testing Exploitation...
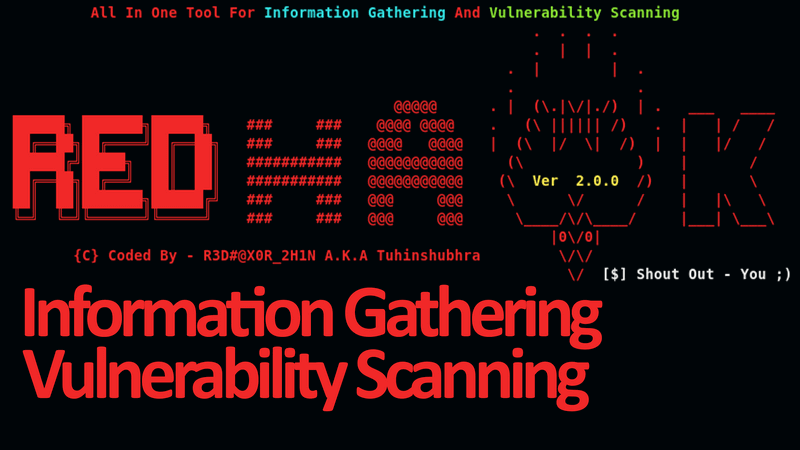
All in one tool for Information Gathering and Vulnerability Scanning RED HAWK : Scans That You Can Perform Using RED HAWK : Basic Scan Site Title NEW IP...
Snowden told Moudeina that he was operating on an app that could turn a mobile device into a kind of motion sensor in form to notify you when your things are...
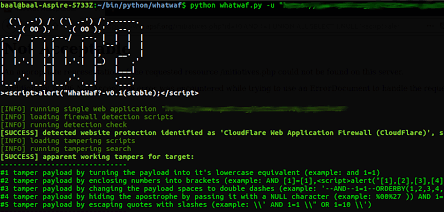
WhatWaf is an advanced firewall detection tool who’s goal is to give you the idea of “There’s a WAF?”. WhatWaf works by detecting a...