[sc name=”ad_1″] A curated list of Android Security materials and resources For Pentesters and Bug Hunters. Blog AAPG – Android application...
Search Results For - Client Side
[sc name=”ad_1″] “MEDUZA” (“медуза”) means “jellyfish” in Ukrainian What is MEDUZA? It’s a Frida...
[sc name=”ad_1″] A set of scripts to help perform an online dictionary attack against a WPA3 access point. Wacker leverages the wpa_supplicant...
[sc name=”ad_1″] Velociraptor is a tool for collecting host based state information using Velocidex Query Language (VQL) queries. To learn more...
[sc name=”ad_1″] A Fast Reverse Proxy To Help You Expose A Local Server Behind A NAT Or Firewall To The Internet. Development Status frp is under...
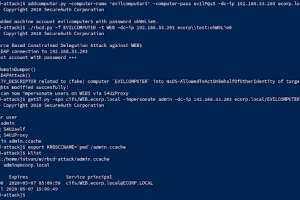
[sc name=”ad_1″] Abusing Kerberos Resource-Based Constrained Delegation TL;DR This repo is about a practical attack against Kerberos Resource-Based...
[sc name=”ad_1″] SNIcat is a proof of concept tool that performs data exfiltration, utilizing a covert channel method via. Server Name Indication...
[sc name=”ad_1″] SkyArk is a cloud security project with two main scanning modules: AzureStealth – Scans Azure environments AWStealth –...
[sc name=”ad_1″] cnitch (snitch or container snitch) is a simple framework and command line tool for monitoring Docker containers to identify any...
[sc name=”ad_1″] Terminal and Web console for Kubernetes Features Configuration from kubeconfig files (KUBECONFIG environment variable or $HOME/...