[sc name=”ad_1″] Every app installed on your smartphone with permission to access location service “can” continually collect your real...
Search Results For - Check
[sc name=”ad_1″] A team of cybersecurity researchers from the University of New Haven yesterday released a video demonstrating how vulnerabilities...
[sc name=”ad_1″] Exclusive — A security researcher has identified an unsecured server that was leaking detailed personal details of nearly half a...
[sc name=”ad_1″] Beware Windows users… a new dangerous remote code execution vulnerability has been discovered in the WinRAR software...
[sc name=”ad_1″] It’s not at all surprising that downloading movies and software from the torrent network could infect your computer with...
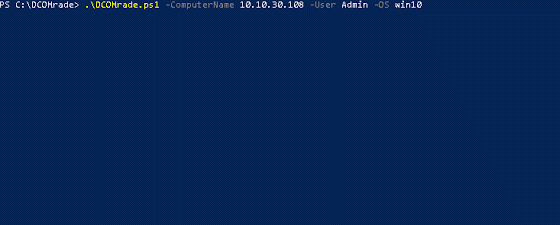
[sc name=”ad_1″] DCOMrade is a Powershell script that is able to enumerate the possible vulnerable DCOM applications that might allow for...
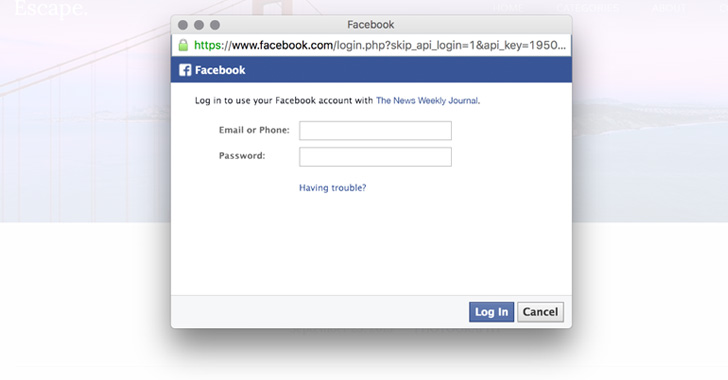
[sc name=”ad_1″] How do you check if a website asking for your credentials is fake or legit to log in? By checking if the URL is correct? By...
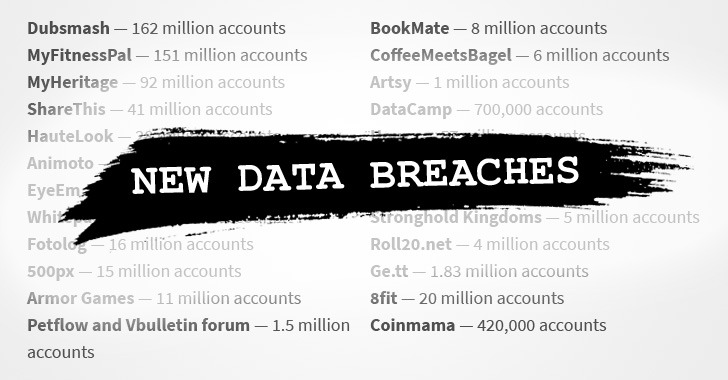
[sc name=”ad_1″] A hacker who was selling details of nearly 620 million online accounts stolen from 16 popular websites has now put up a second...
[sc name=”ad_1″] Cybersecurity researchers have discovered a way to hide malicious code in Intel SGX enclaves, a hardware-based memory encryption...
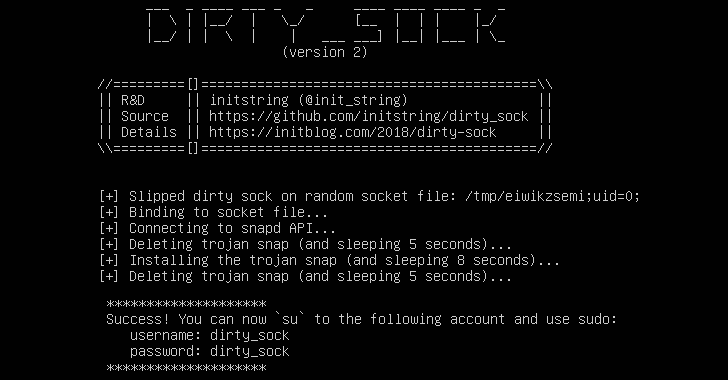
[sc name=”ad_1″] Ubuntu and some other Linux distributions suffer from a severe privilege escalation vulnerability that could allow a local...