Nameles provides an easy to deploy, scalable IVT detection and filtering solution that is proven to detect at a high level of accuracy ad fraud and other types...
Search Results For - Boot Time
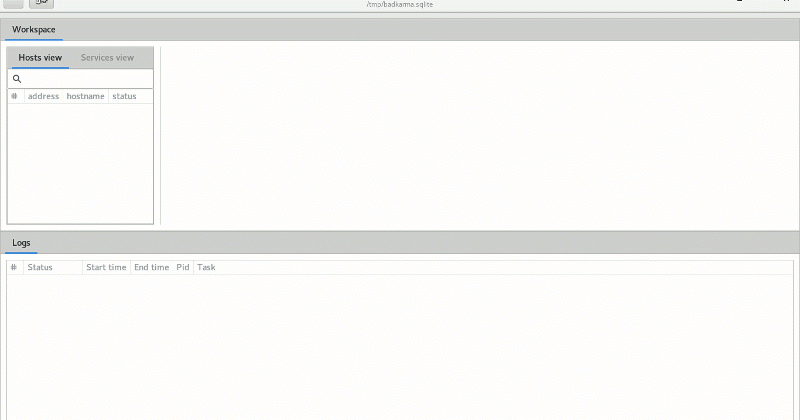
badKarma is a python3 GTK+ network infrastructure penetration testing toolkit. badKarma aim to help the tester in all the penetration testing phases...
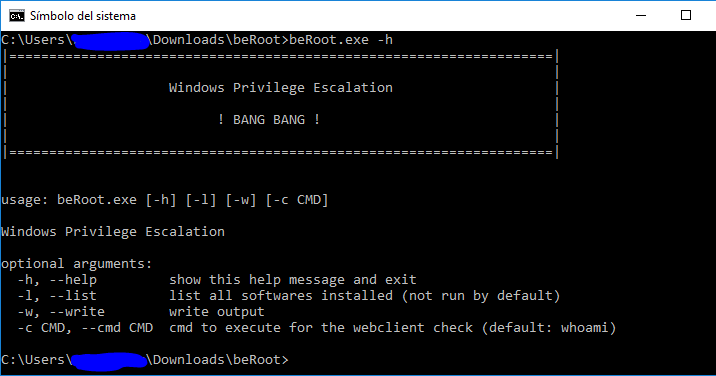
BeRoot(s) is a post exploitation tool to check common Windows misconfigurations to find a way to escalate our privilege. A compiled version is available here...
Red Team Arsenal is a web/network security scanner which has the capability to scan all company’s online facing assets and provide an holistic security view of...
Hacking requires a lot of brainstorming since you need a robust machine that will not lag or run out of resources during working. Hacking involves DDOS a...
Raspberry Pi 3 Model B+ is now on sale for $35 (the same price as the existing Raspberry Pi 3 Model B), featuring: A 1.4GHz 64-bit quad-core ARM Cortex-A53 CPU...
Kali Linux 2018.1 the first release of 2018, this fine release contains all updated packages and bug fixes since our 2017.3 release last November. This release...
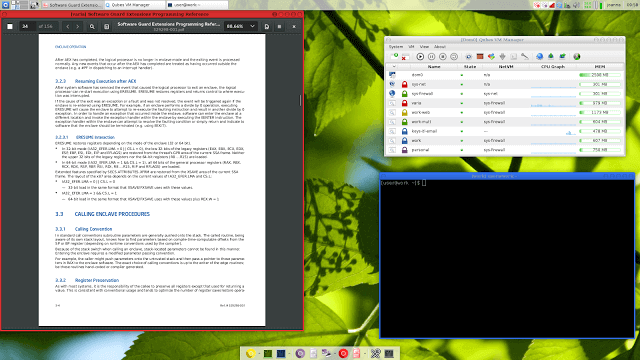
Qubes OS is a security-oriented operating system (OS). The OS is the software that runs all the other programs on a computer. Some examples of popular OSes are...
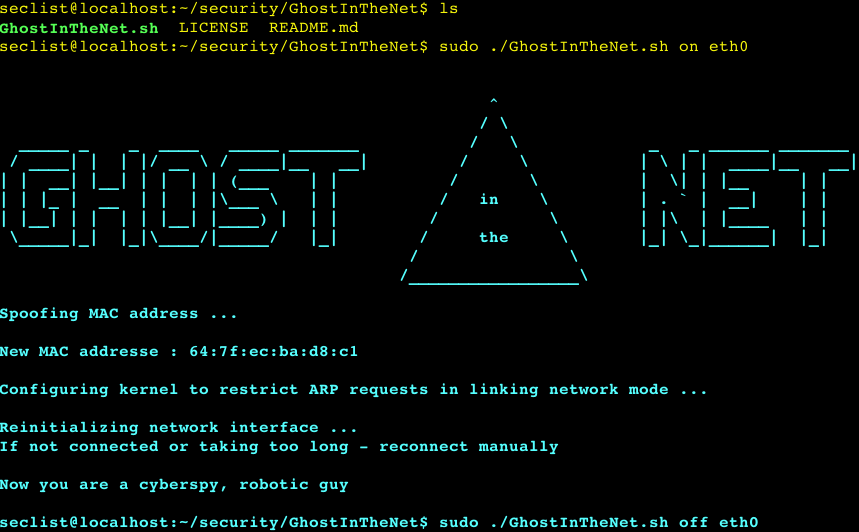
Ultimate Network Stealther that makes Linux a Ghost In The Net and protects from MITM/DOS/scan. Properties: Network Invisibility Network Anonymity Protects...
Security researchers from Kaspersky have discovered a new malware that is targeting Android phones. This malware, called as Loapi, is a harmful piece of code...