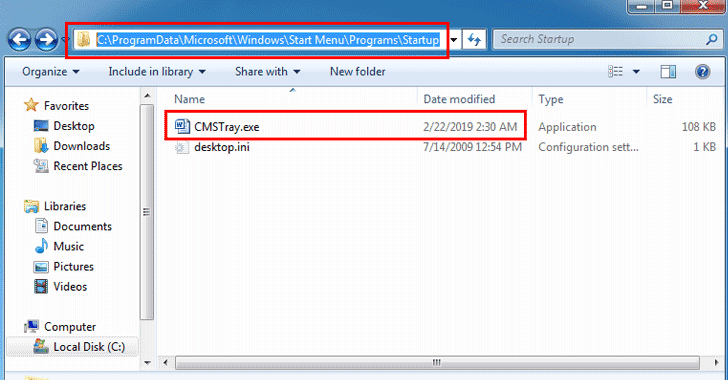
[sc name=”ad_1″] The Metasploit Project is a computer security project that provides information on vulnerabilities, helping in the development of...
Search Results For - Boot Time
[sc name=”ad_1″] It’s not just the critical Drupal vulnerability that is being exploited by in the wild cybercriminals to attack vulnerable...
[sc name=”ad_1″] You’ve always been warned not to share remote access to your computer with any untrusted people for many reasons—it’s...
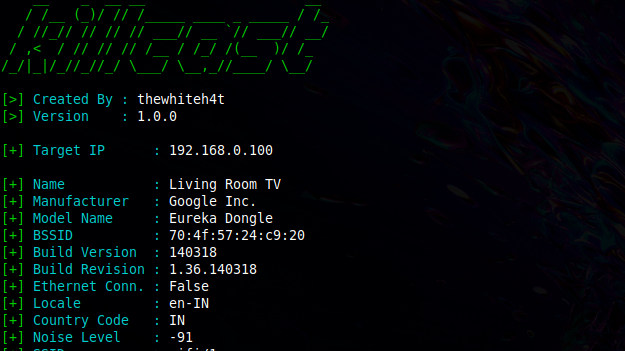
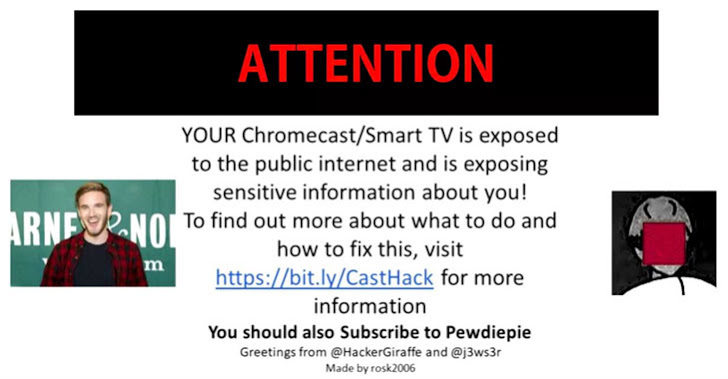
[sc name=”ad_1″] Manipulate Chromecast Devices in your Network. Inspiration – Thousands of Google Chromecast Devices Hijacked to Promote...
[sc name=”ad_1″] A group of hackers has hijacked tens of thousands of Google’s Chromecast streaming dongles, Google Home smart speakers and...
[sc name=”ad_1″] Shamoon is back… one of the most destructive malware families that caused damage to Saudi Arabia’s largest oil producer in...
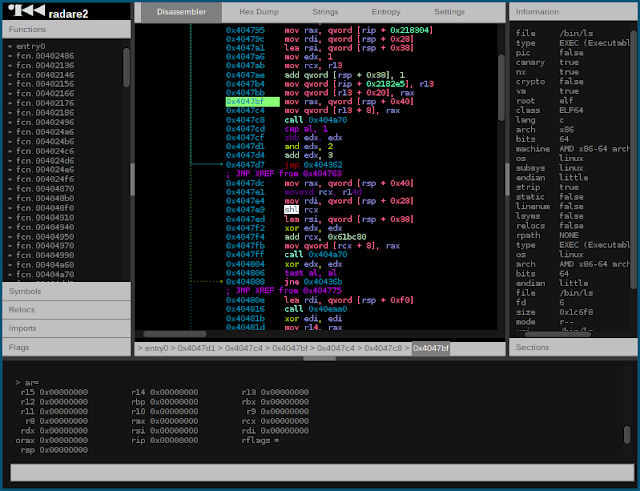
[sc name=”ad_1″] r2 is a rewrite from scratch of radare in order to provide a set of libraries and tools to work with binary files. Radare...
[sc name=”ad_1″] The real identity of Tessa88—the notorious hacker tied to several high-profile cyber attacks including the LinkedIn, DropBox and...
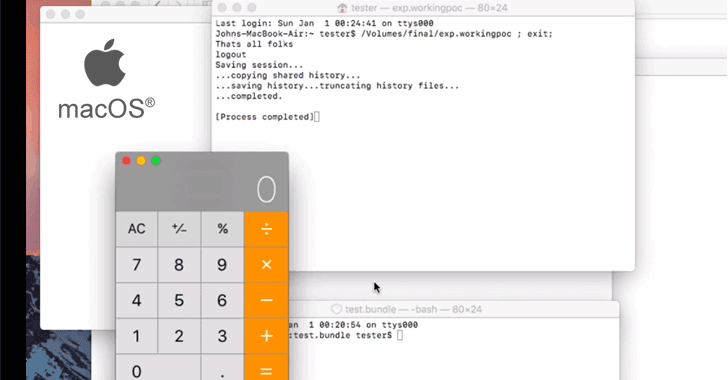
[sc name=”ad_1″] Earlier this week Dropbox team unveiled details of three critical vulnerabilities in Apple macOS operating system, which...
ACHE is a focused web crawler. It collects web pages that satisfy some specific criteria, e.g., pages that belong to a given domain or that contain a user...