[sc name=”ad_1″] Hardened Debian GNU/Linux and CentOS 8 distro auditing. The main test environment is in debian GNU/Linux 9/10 and CentOS 8, and...
Search Results For - Arch Linux
[sc name=”ad_1″] Espionage is a network packet sniffer that intercepts large amounts of data being passed through an interface. The tool allows...
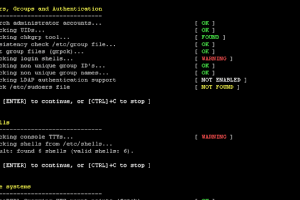
[sc name=”ad_1″] We are excited to announce this major release of auditing tool Lynis. Several big changes have been made to core functions of...
[sc name=”ad_1″] KeyLogger for Linux Systems. Features Runs on GUI systems or CLI Sending data by email Dependencies curl libx11-dev (Debian-Based)...
[sc name=”ad_1″] Impost3r is a tool that aim to steal many kinds of linux passwords(including ssh,su,sudo) written by C. Attackers can use Impost3r...
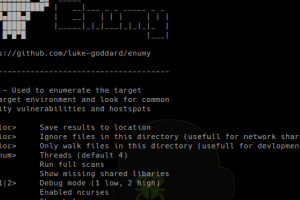
[sc name=”ad_1″] Enumy is portable executable that you drop on target Linux machine during a pentest or CTF in the post exploitation phase. Running...
[sc name=”ad_1″] We are incredibly excited to announce the second release of 2020, Kali Linux 2020.2 A quick overview of what’s new since January:...
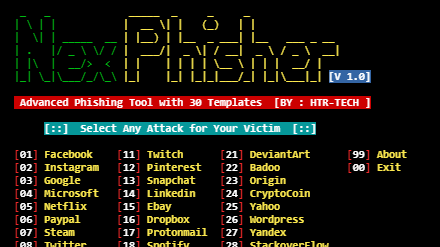
[sc name=”ad_1″] NexPhisher is an automated Phishing tool made for Termux & Linux .The phishing Pages are Taken from Zphisher under GNU General...
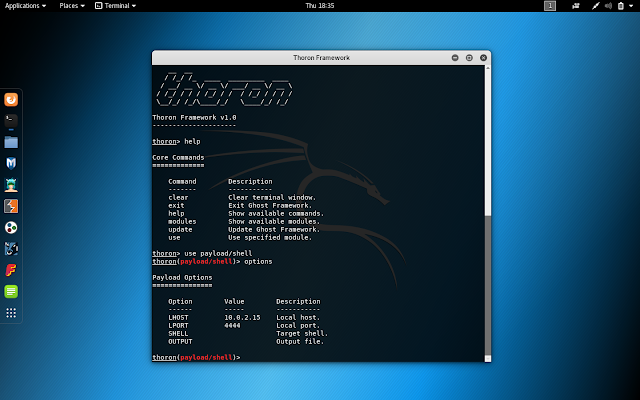
[sc name=”ad_1″] About Thoron Framework Thoron Framework is a Linux post-exploitation framework that exploit Linux tcp vulnerability to get shell...
[sc name=”ad_1″] FileSystem Monitor utility that runs on Linux, Android, iOS and OSX. Brought to you by Sergi Àlvarez at Nowsecure and distributed...