[sc name=”ad_1″] Hey Guys, In this video i show you how to Embed a Metasploit Payload in an Original .Apk File. Normally we have to install the...
Search Results For - Android
This will be the beggining of a long series of the basics of linux, so let’s get started. What is Linux? Open-Source? What is the use of Linux? Linux is...
Nmap (“Network Mapper”) is a free and open source utility for network discovery and security auditing. Many systems and network administrators also...
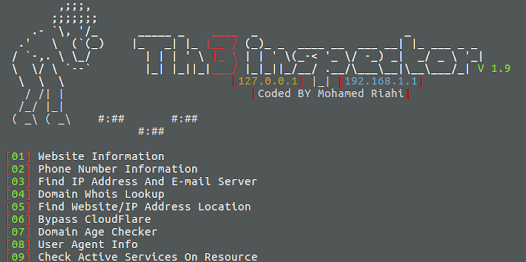
Tool For Information Gathering. Usage Short Form Long Form Description -i –info Website Information -n –number Phone Number Information -mx...
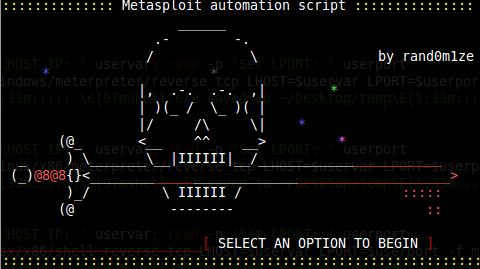
Command line script for automating metasploit functions: Checks for metasploit service and starts if not present Easily craft meterpreter reverse_tcp...
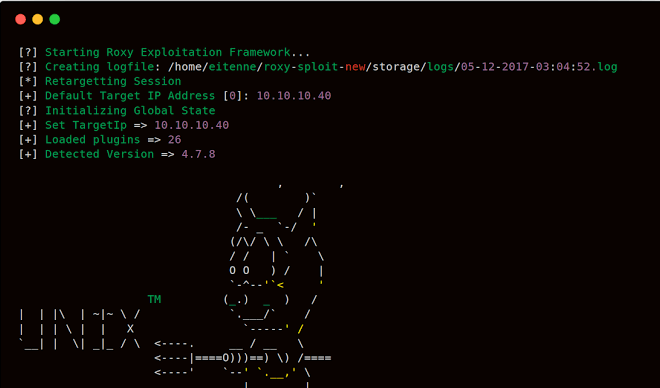
roxysploit is a community-supported, open-source and penetration testing suite that supports attacks for numerous scenarios. conducting attacks in the field...
The group, which embodies countless tech organizations including Google, Amazon, Facebook, Etsy and various companies, stated that the organization will not...
QuarkslaB Dynamic binary Instrumentation (QBDI) is a modular, cross-platform and cross-architecture DBI framework. It aims to support Linux, macOS, Android...
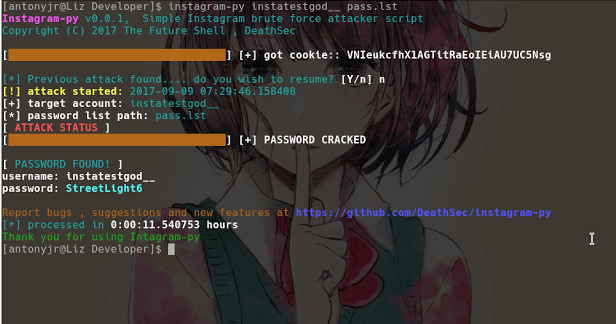
Instagram-Py is a simple python script to perform basic brute force attack against Instagram , this script can bypass login limiting on wrong passwords , so...
Qubes OS is a security-oriented operating system (OS). The OS is the software that runs all the other programs on a computer. Some examples of popular OSes are...