This Kali release is the first to include the Linux 4.15 kernel, which includes the x86 and x64 fixes for the much-hyped Spectre and Meltdown vulnerabilities...
Search Results For - Access
The single most common causes of a broken Kali Linux installation are following unofficial advice, and particularly arbitrarily populating the system’s sources...
M$ Windows Hacking Pack =========== Tools here are from different sources. The repo is generally licensed with WTFPL, but some content may be not (eg...
Hey Guys, In this video i show you how to perform Wi-Fi deauthentication attack on any Wi-Fi Network. Wi-Fi deauthentication attack is a type of denial-of...
p0wnedShell is an offensive PowerShell host application written in C# that does not rely on powershell.exe but runs powershell commands and functions within a...
This is Part 2 of Linux Basics In this Part we will talk about your first steps with linux. Logging In and Out: The Linux system distinguishes between...
This will be the beggining of a long series of the basics of linux, so let’s get started. What is Linux? Open-Source? What is the use of Linux? Linux is...
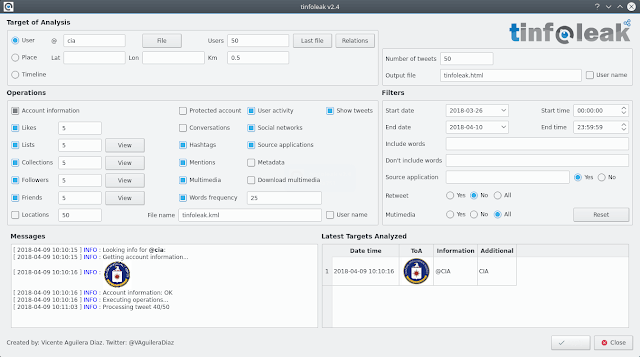
The most complete open-source tool for Twitter intelligence analysis Introduction tinfoleak is an open-source tool within the OSINT (Open Source Intelligence)...
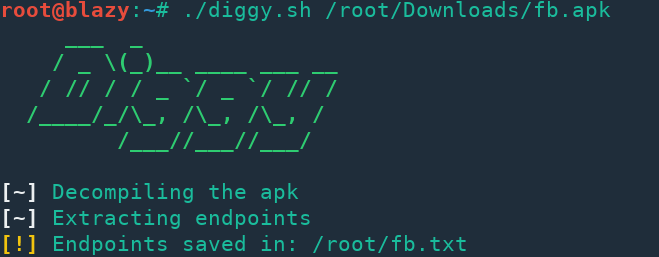
Diggy can extract endpoints/URLs from apk files. It saves the result into a txt file for further processing. Dependencies apktool Usage ./diggy.sh...
Author: Colin Harper If you’ve ever dealt in Bitcoin, you may have suffered through hour-long (or at worst, day-long) transaction times. It’s becoming...