[sc name=”ad_1″] The US Department of Justice on Thursday charged two Chinese hackers associated with the Chinese government for hacking numerous...
Search Results For - Access
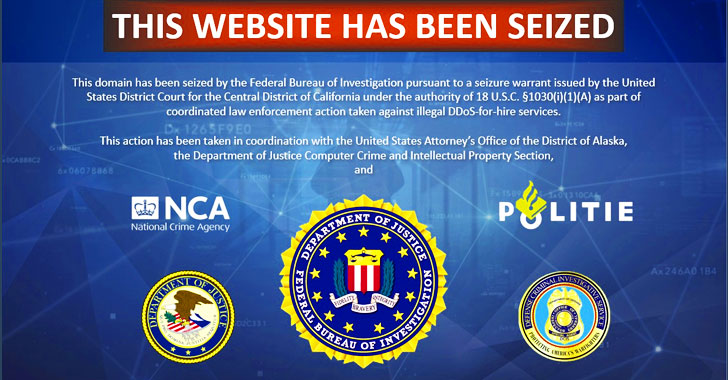
[sc name=”ad_1″] The FBI just saved the Christmas. The U.S. Justice Department announced earlier today that the FBI has seized domains of 15...
[sc name=”ad_1″] Microsoft today issued an out-of-band security update to patch a critical zero-day vulnerability in Internet Explorer (IE) Web...
[sc name=”ad_1″] Another day, another data breach. This time it’s the United States National Aeronautics and Space Administration (NASA) NASA...
[sc name=”ad_1″] Twitter has been hit with a minor data breach incident that the social networking site believes linked to a suspected state...
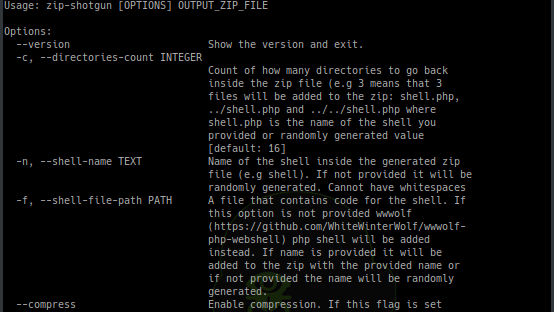
[sc name=”ad_1″] Utility script to test zip file upload functionality (and possible extraction of zip files) for vulnerabilities. Idea for this...
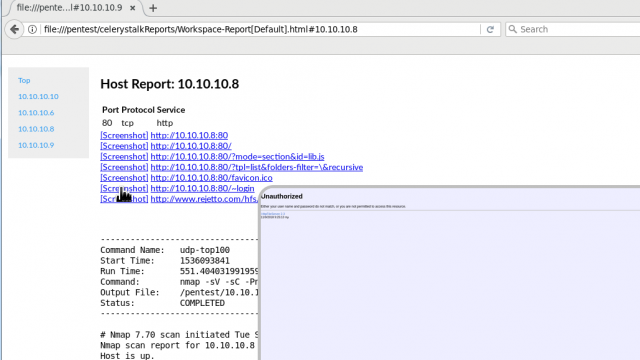
[sc name=”ad_1″] celerystalk helps you automate your network scanning/enumeration process with asynchronous jobs (aka tasks) while retaining full...
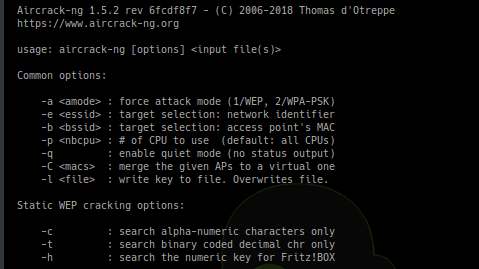
[sc name=”ad_1″] Aircrack-ng is a complete suite of tools to assess WiFi network security. It focuses on different areas of WiFi security:...
[sc name=”ad_1″] Facebook’s latest screw-up — a programming bug in Facebook website accidentally gave 1,500 third-party apps access to the...
[sc name=”ad_1″] One Security vulnerability assessment/management tool to solve all the security team problems. What is Jackhammer? Jackhammer is a...