[sc name=”ad_1″] The world of cybersecurity is fast-paced and ever-changing. New attacks are unleashed every day, and companies around the world...
Search Results For - Access
[sc name=”ad_1″] The Metasploit Project is a computer security project that provides information on vulnerabilities, helping in the development of...
[sc name=”ad_1″] It’s not just the critical Drupal vulnerability that is being exploited by in the wild cybercriminals to attack vulnerable...
[sc name=”ad_1″] Great news. If you have already installed the latest update of Google Play Services released earlier today, and your Android...
[sc name=”ad_1″] Every app installed on your smartphone with permission to access location service “can” continually collect your real...
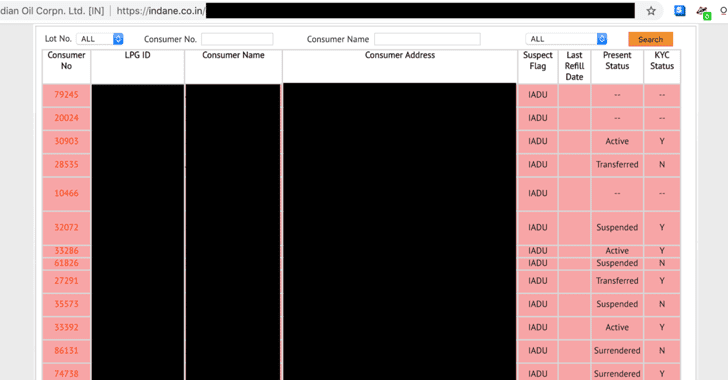
[sc name=”ad_1″] Exclusive — A security researcher has identified an unsecured server that was leaking detailed personal details of nearly half a...
[sc name=”ad_1″] Exclusive — If you have not updated your website to the latest WordPress version 5.0.3, it’s a brilliant idea to upgrade the...
[sc name=”ad_1″] Why would someone bother to hack a so-called “ultra-secure encrypted database that is being protected behind 13 feet high...
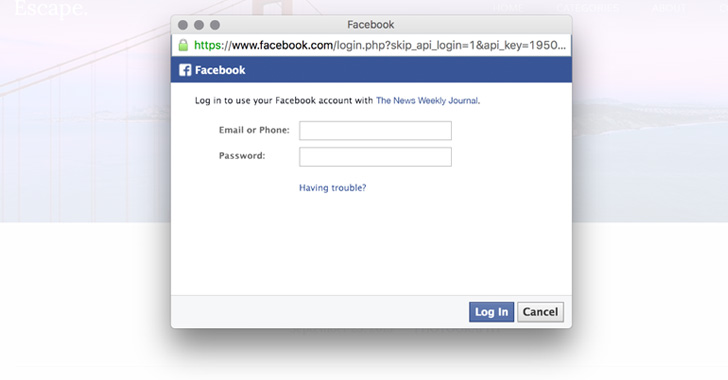
[sc name=”ad_1″] It’s 2019, and just clicking on a specially crafted URL would have allowed an attacker to hack your Facebook account without...
[sc name=”ad_1″] How do you check if a website asking for your credentials is fake or legit to log in? By checking if the URL is correct? By...