The security vulnerability was discovered in the Linksys WVBR0-25 wireless video bridge, which was designed to enable the main Genie DVR to communicate over...
Search Results For - AWS
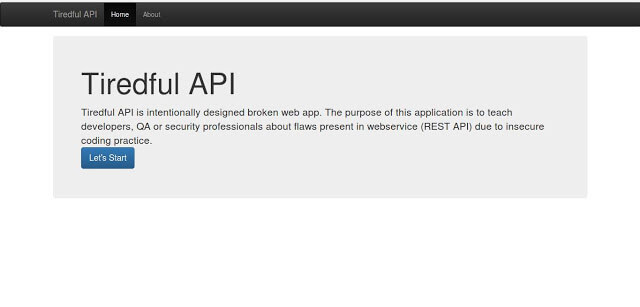
Tiredful API is intentionally designed broken app. The aim of this web app is to teach developers, QA or security professionals about flaws present in...
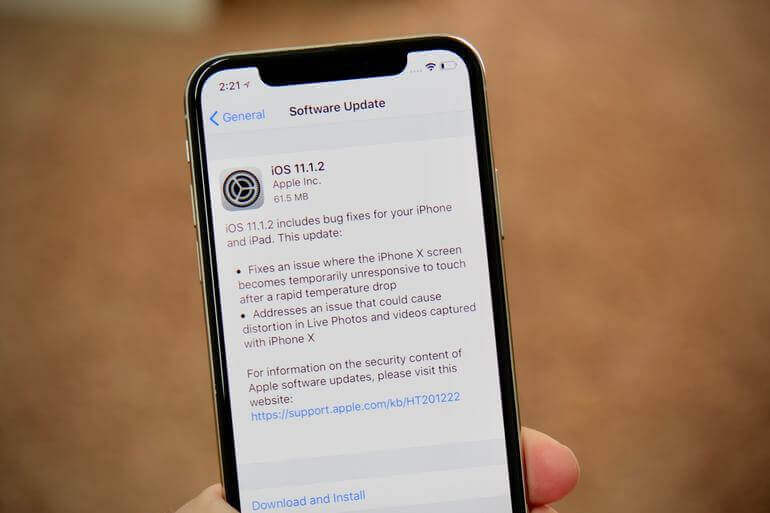
Google’s Project Zero iOS bug hunter Ian Beer has released details about an iOS 11 exploit that could offer up a jailbreak for iOS 11.1.2. Beer last week...
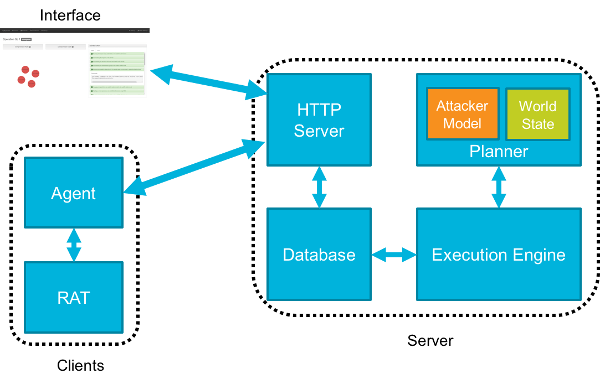
CALDERA is an automated adversary emulation system that performs post-compromise adversarial behavior within enterprise networks. It generates plans during...
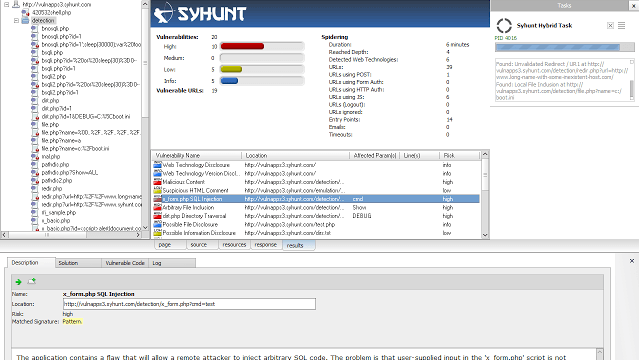
Syhunt ScanTools 6.0 adds advanced fingerprinting capabilities, enhanced spidering, injection and code scan capabilities, and a large number of improved checks...
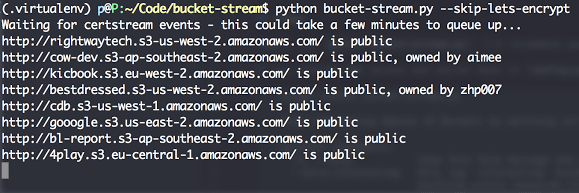
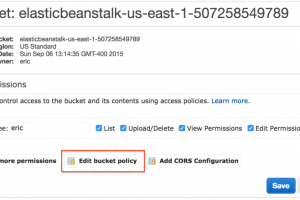
Some quick tips if you use S3 buckets: Randomise your bucket names! There is no need to use company-backup.s3.amazonaws.com. Set appropriate permissions and...
The group, called Google You Owe Us, said in a declaration Thursday that it was the first case of its sort in the U.K. against a major tech business over the...
The business allowed 57 people to drive vehicles although they required valid driver’s licenses or had performed other offenses that would have excluded them...
It had earlier banned an internet-associated doll called, My Friend Cayla, for similar reasons. Telecoms regulator the Federal Network Agency urged parents who...
Discovered by UpGuard defense researcher Chris Vickery, the databases were entitled “CENTCOM-backup,” “CENTCOM-archive,” and “pacom-archive.” Based on their...