This will be the beggining of a long series of the basics of linux, so let’s get started. What is Linux? Open-Source? What is the use of Linux? Linux is...
Search Results For - /Linux
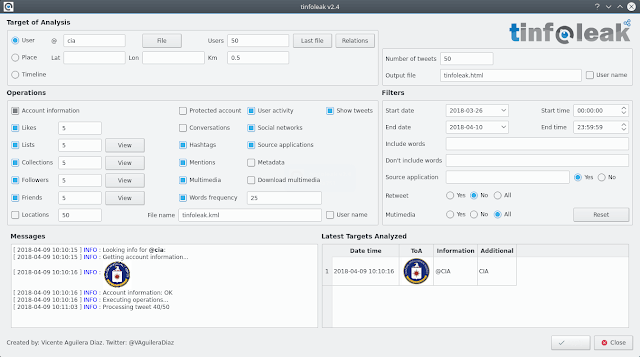
The most complete open-source tool for Twitter intelligence analysis Introduction tinfoleak is an open-source tool within the OSINT (Open Source Intelligence)...
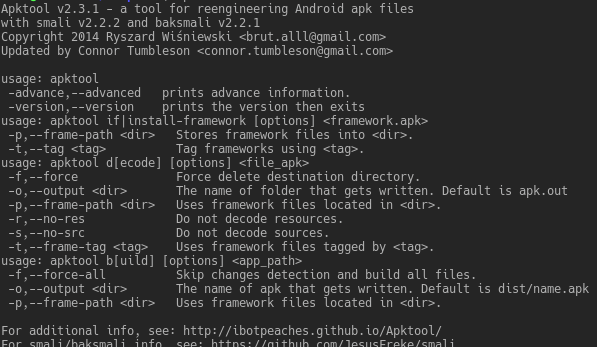
A tool for reverse engineering 3rd party, closed, binary Android apps. It can decode resources to nearly original form and rebuild them after making some...
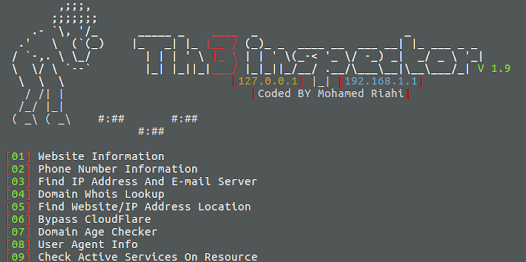
Tool For Information Gathering. Usage Short Form Long Form Description -i –info Website Information -n –number Phone Number Information -mx...
GlobaLeaks is an open-source, free software intended to enable secure and anonymous whistleblowing initiatives developed by the Hermes Center for Transparency...
As the name might suggest AutoSploit attempts to automate the exploitation of remote hosts. Targets are collected automatically as well by employing the Shodan...
The Automated Collection and Enrichment (ACE) platform is a suite of tools for threat hunters to collect data from many endpoints in a network and...
Speculative optimizations execute code in a non-secure manner leaving data traces in microarchitecture such as cache. Refer to the paper by Lipp et. al 2017...
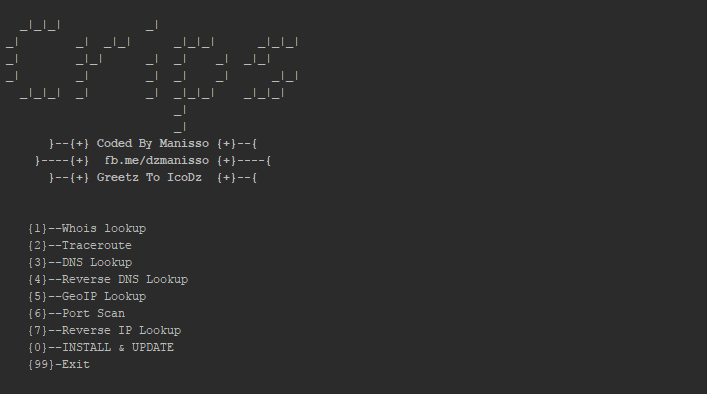
This Tools is a collection of online IP Tools that can be used to quickly get information about IP Address’s, Web Pages and DNS records. Menu Whois...
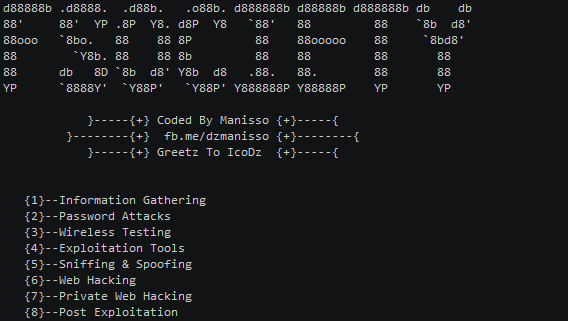
A Penetration Testing Framework , you will have every script that a hacker needs Menu Information Gathering Password Attacks Wireless Testing Exploitation...