[sc name=”ad_1″] nginx Docker image secure by default. Avoid the hassle of following security best practices each time you need a web server or...
Search Results For - /Brute Force
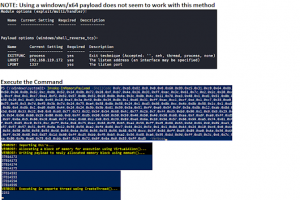
[sc name=”ad_1″] Easy brute forcing to whatever you want, Its magic increasing values and direct. Implementation Clone git clone Download the...
[sc name=”ad_1″] What the heck is a ferox anyway? Ferox is short for Ferric Oxide. Ferric Oxide, simply put, is rust. The name rustbuster was...
[sc name=”ad_1″] Collection of PowerShell functions a Red Teamer may use to collect data from a machine or gain access to a target. I added ps1...
[sc name=”ad_1″] jwt-hack is tool for hacking / security testing to JWT. Supported for En/decoding JWT, Generate payload for JWT attack and very...
[sc name=”ad_1″] RmiTaste allows security professionals to detect, enumerate, interact and attack RMI services by calling remote methods with...
[sc name=”ad_1″] h2cSmuggler smuggles HTTP traffic past insecure edge-server proxy_pass configurations by establishing HTTP/2 cleartext (h2c)...
[sc name=”ad_1″] A set of scripts to help perform an online dictionary attack against a WPA3 access point. Wacker leverages the wpa_supplicant...
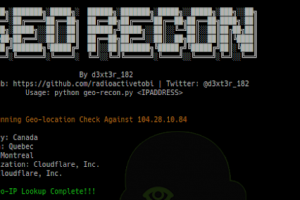
[sc name=”ad_1″] An OSINT CLI tool desgined to fast track IP Reputation and Geo-locaton look up for Security Analysts. Setup This tool is...
[sc name=”ad_1″] Tested environments: Windows, MAC, linux, and windows subsystem for linux (WSL) What can SourceWolf do? Crawl through responses to...