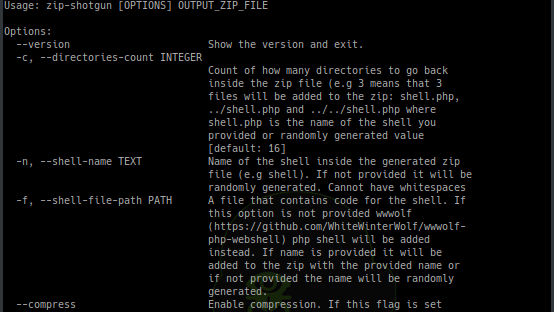
[sc name=”ad_1″] Utility script to test zip file upload functionality (and possible extraction of zip files) for vulnerabilities. Idea for this script comes...
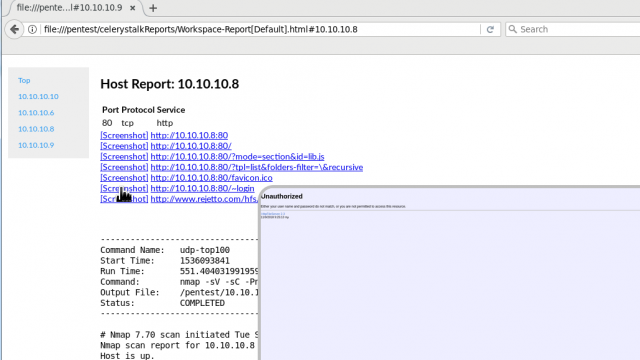
[sc name=”ad_1″] celerystalk helps you automate your network scanning/enumeration process with asynchronous jobs (aka tasks) while retaining full control of...
[sc name=”ad_1″] Cybersecurity researchers have discovered a critical vulnerability in widely used SQLite database software that exposes billions of...
[sc name=”ad_1″] Shamoon is back… one of the most destructive malware families that caused damage to Saudi Arabia’s largest oil producer in 2012 and...
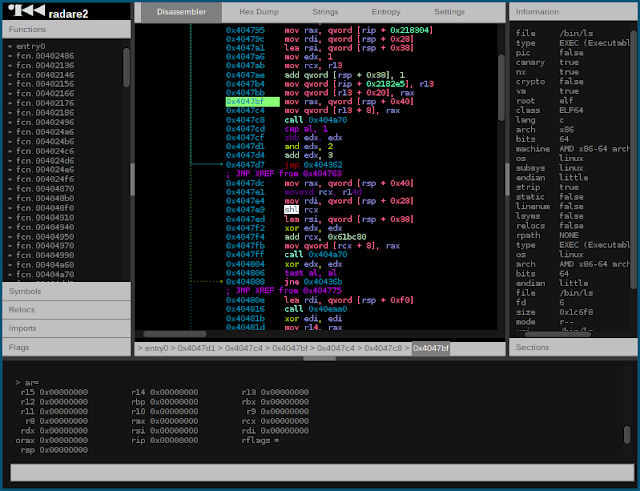
[sc name=”ad_1″] r2 is a rewrite from scratch of radare in order to provide a set of libraries and tools to work with binary files. Radare project...
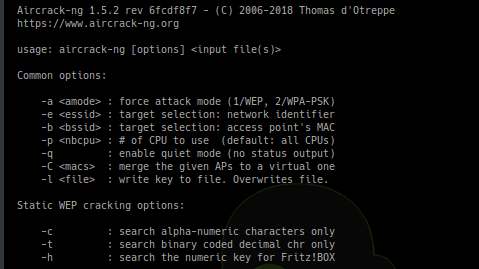
[sc name=”ad_1″] Aircrack-ng is a complete suite of tools to assess WiFi network security. It focuses on different areas of WiFi security: Monitoring: Packet...
[sc name=”ad_1″] Facebook’s latest screw-up — a programming bug in Facebook website accidentally gave 1,500 third-party apps access to the unposted...
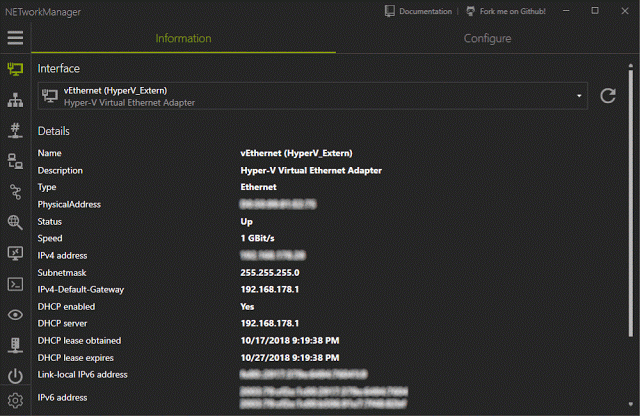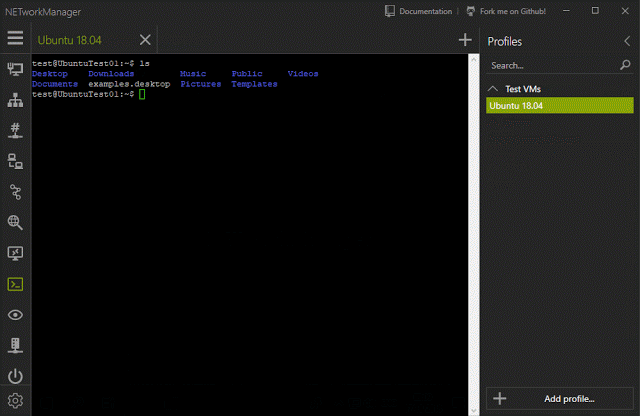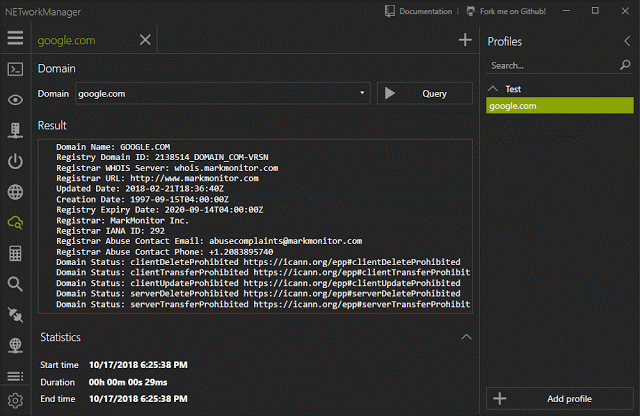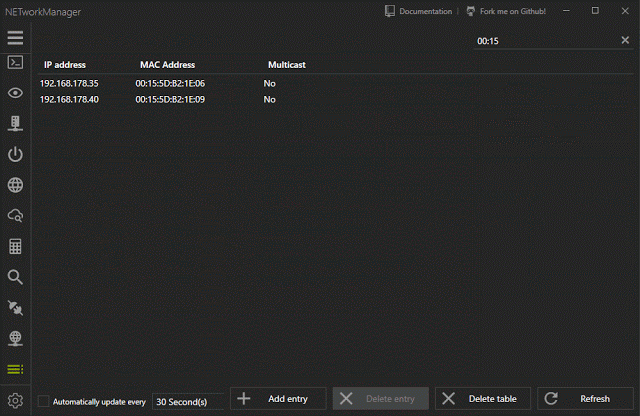
[sc name=”ad_1″] A powerful tool for managing networks and troubleshoot network problems! Features Network Interface – Information, Configure IP...
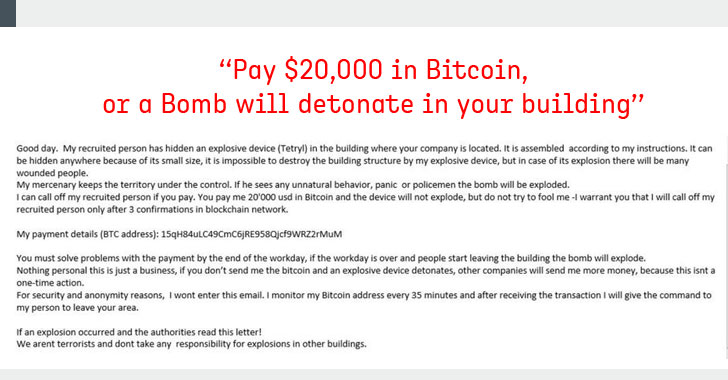
[sc name=”ad_1″] “Pay $20,000 worth of bitcoin, or a bomb will detonate in your building” A massive number of businesses, schools, government...
[sc name=”ad_1″] One Security vulnerability assessment/management tool to solve all the security team problems. What is Jackhammer? Jackhammer is a...