[sc name=”ad_1″] Cynet goes head-to-head with CrowdStrike, DarkTrace, Cylance, Carbon Black & Symantec, offering their unhappy customers a refund for the...
[sc name=”ad_1″] It’s time for another batch of “Patch Tuesday” updates from Microsoft. Microsoft today released its March 2019 software...
[sc name=”ad_1″] Adobe users would feel lighter this month, as Adobe has released patches for just two security vulnerability in its March Security Update...
[sc name=”ad_1″] Do you always think twice before installing Windows updates worrying that it could crash your system or leave it non-working the day after...
[sc name=”ad_1″] Popular enterprise software company Citrix that provides services to the U.S. military, the FBI, many U.S. corporations, and various U.S...
[sc name=”ad_1″] With countless web apps and online services launching every day, there is an increasing demand for cloud developers. This exciting niche is...
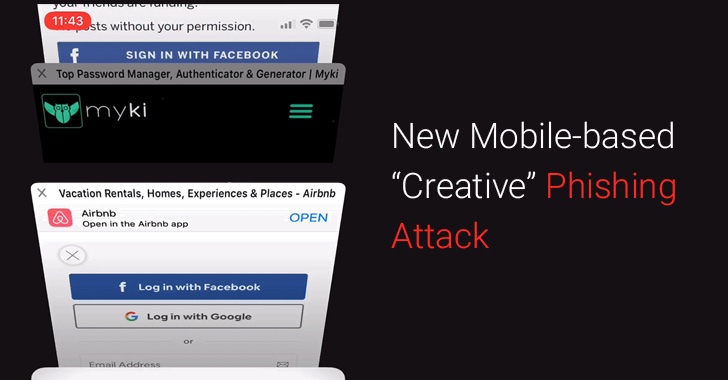
[sc name=”ad_1″] A cybersecurity researcher who last month warned of a creative phishing campaign has now shared details of a new but similar attack campaign...
[sc name=”ad_1″] A security researcher has discovered a severe vulnerability in the popular, open source event-driven platform StackStorm that could allow...
[sc name=”ad_1″] The United States’ National Security Agency (NSA) today finally released GHIDRA version 9.0 for free, the agency’s home-grown...
[sc name=”ad_1″] You must update your Google Chrome immediately to the latest version of the web browsing application. Security researcher Clement Lecigne of...