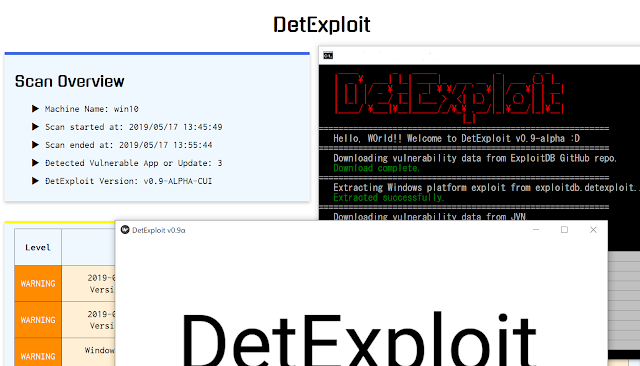
[sc name=”ad_1″] DetExploit is software that detect vulnerable applications and not-installed important OS updates on the system, and notify them to user. As...
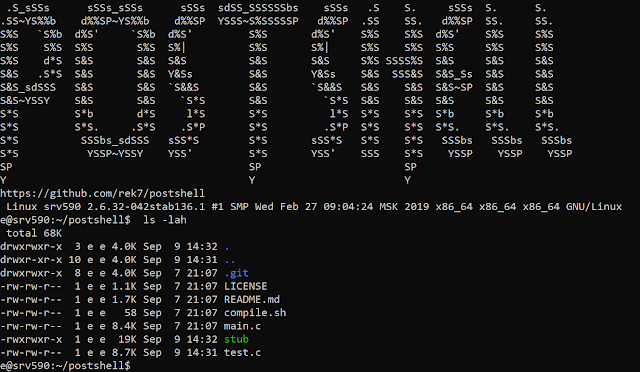
[sc name=”ad_1″] PostShell is a post-exploitation shell that includes both a bind and a back connect shell. It creates a fully interactive TTY which allows...
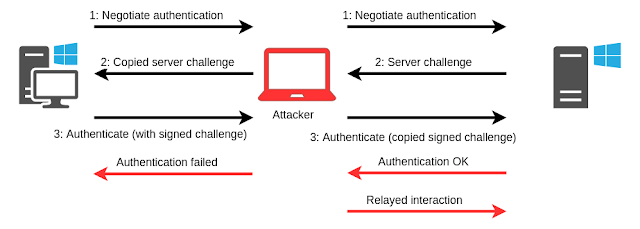
[sc name=”ad_1″] POC tools accompanying the blog Abusing Exchange: One API call away from Domain Admin. Requirements These tools require impacket. You can...
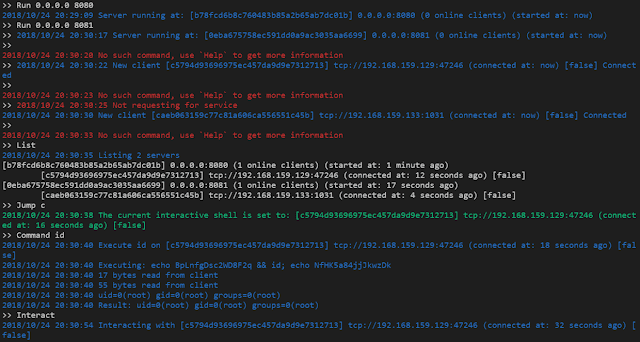
[sc name=”ad_1″] A modern multiple reverse shell sessions/clients manager via terminal written in go. Features Multiple service listening port Multiple...
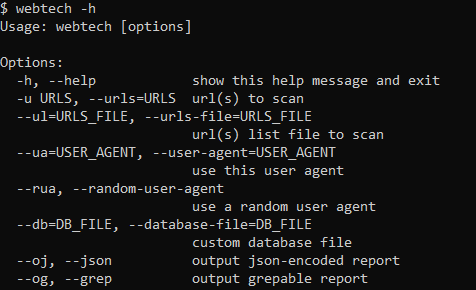
[sc name=”ad_1″] We knew that there are already tools doing this, for example Wappalyzer or CERN’s WAD, but we wanted a modular tool capable of reading...
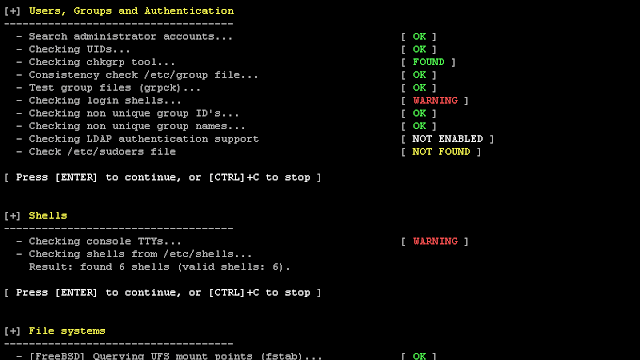
[sc name=”ad_1″] We are excited to announce this major release of auditing tool Lynis. Several big changes have been made to core functions of Lynis. These...
[sc name=”ad_1″] Google announced some major changes for its Android mobile operating system in October after the European Commission hit the company with a...
[sc name=”ad_1″] Cybersecurity researchers today disclosed details of two newly identified Magecart attacks targeting online shoppers of bedding retailers...
[sc name=”ad_1″] The popular SSH client program PuTTY has released the latest version of its software that includes security patches for 8 high-severity...
[sc name=”ad_1″] Security researchers have uncovered a new variant of the infamous Mirai Internet of Things botnet, this time targeting embedded devices...