[sc name=”ad_1″] metame is a simple metamorphic code engine for arbitrary executables. From Wikipedia: Metamorphic code is code that when run outputs a...
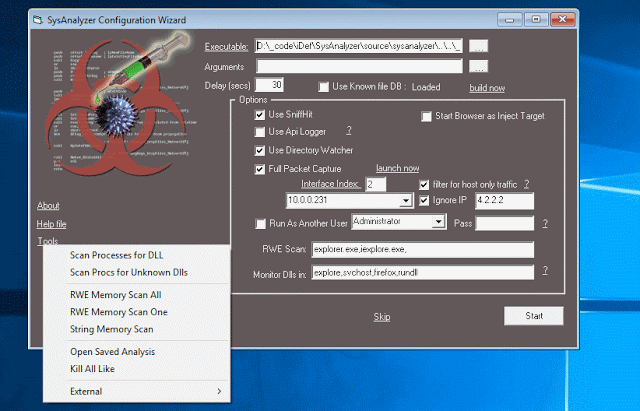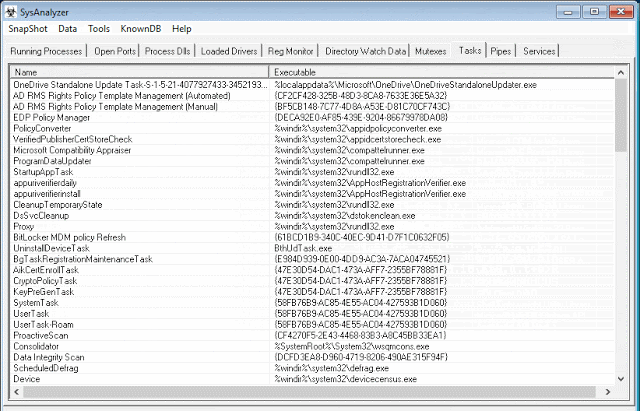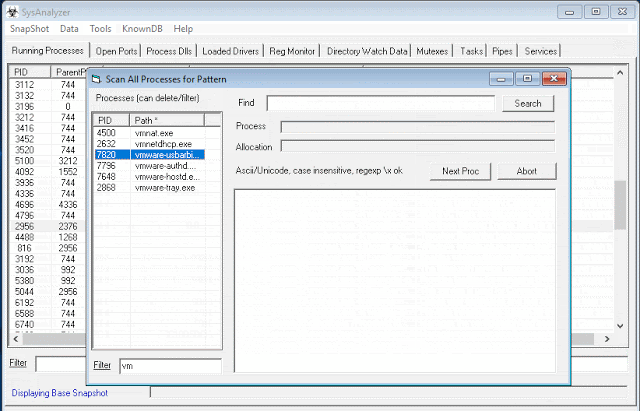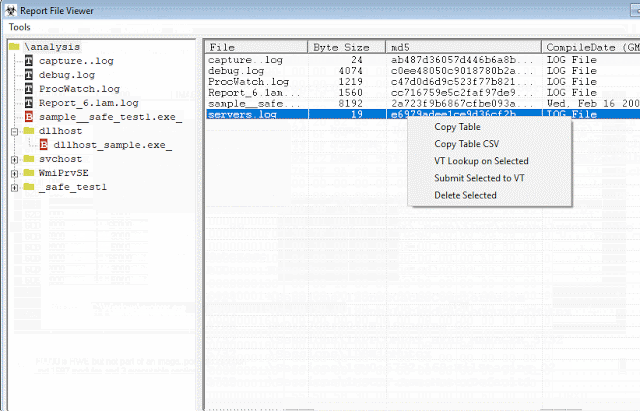
[sc name=”ad_1″] SysAnalyzer is an open-source application that was designed to give malcode analysts an automated tool to quickly collect, compare, and...
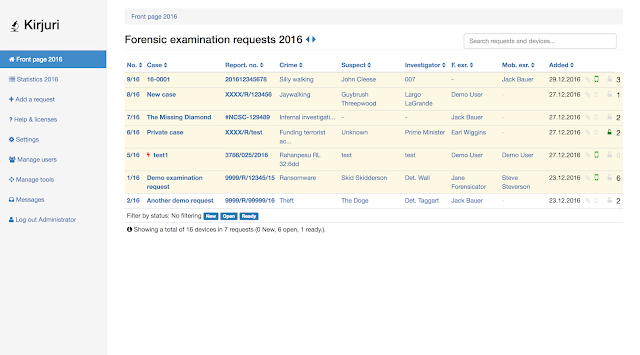
[sc name=”ad_1″] Kirjuri is a simple php/mysql web application for managing physical forensic evidence items. It is intended to be used as a workflow tool...
[sc name=”ad_1″] It is utmost important for any security engineer to understand their network first before securing it and it becomes a daunting task to have...
[sc name=”ad_1″] BOtB is a container analysis and exploitation tool designed to be used by pentesters and engineers while also being CI/CD friendly with...
[sc name=”ad_1″] Aura Botnet C2 Server The botnet’s C2 server utilizes the Django framework as the backend. It is far from the most efficient web...
[sc name=”ad_1″] Dolos Cloak is a python script designed to help network penetration testers and red teamers bypass 802.1x solutions by using an advanced man...
[sc name=”ad_1″] Set of tools for creating/injecting payload into images. Useful references for better understanding of pixload and its use-cases: Bypassing...
[sc name=”ad_1″] Background A while back I was challenged to write a discovery tool with Python3 that could automate the process of finding sensitive...
[sc name=”ad_1″] OpenCTI is an open source platform allowing organizations to manage their cyber threat intelligence knowledge and observables. It has been...