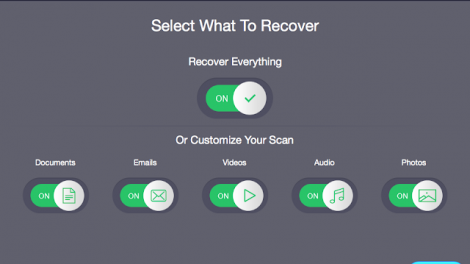
[sc name=”ad_1″] There are many scenarios where you would want to recover deleted data from your Mac. These deleted files could be your important photos...
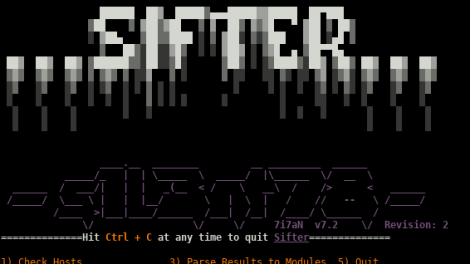
[sc name=”ad_1″] Sifter is a osint, recon & vulnerability scanner. It combines a plethara of tools within different module sets in order to quickly...
[sc name=”ad_1″] Sherlock, a powerful command line tool provided by Sherlock Project, can be used to find usernames across many social networks. It requires...
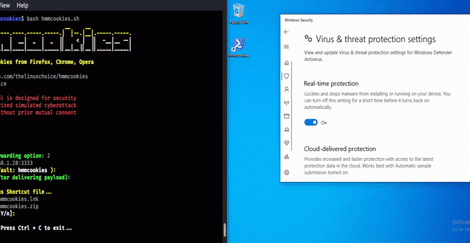
[sc name=”ad_1″] Grab cookies from Firefox, Chrome, Opera using a shortcut file (bypass UAC) Legal disclaimer: Usage of HMMCOOKIES for attacking targets...
[sc name=”ad_1″] Prior to pandemic days, the restaurant industry talked of computers that might end up taking over their daily responsibilities. They’d joke...
[sc name=”ad_1″] A security testing tool to facilitate GraphQL technology security auditing efforts. InQL can be used as a stand-alone script or as a Burp...
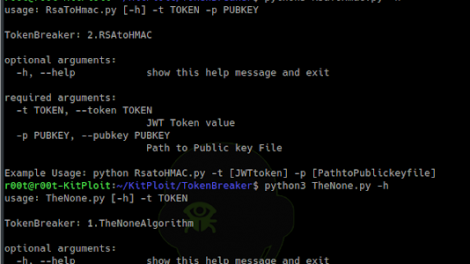
[sc name=”ad_1″] Token Breaker is focused on 2 particular vulnerability related to JWT tokens. None Algorithm RSAtoHMAC Refer to this link about insights of...
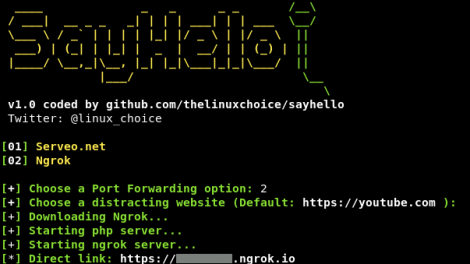
[sc name=”ad_1″] Capturing audio (.wav) from target using a link How it works? After the user grants microphone permissions, a website redirect button of...
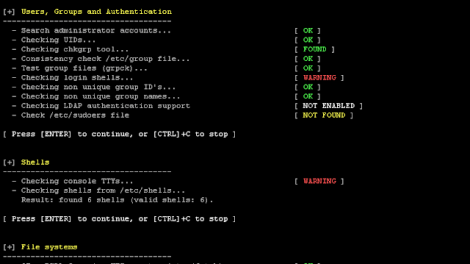
[sc name=”ad_1″] We are excited to announce this major release of auditing tool Lynis. Several big changes have been made to core functions of Lynis. These...
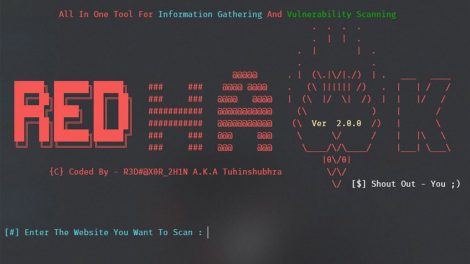
All in one tool for Information Gathering, Vulnerability Scanning and Crawling. A must have tool for all penetration testers. Scans That You Can Perform Using RED HAWK...