[sc name=”ad_1″] A (Still in Development) monitoring browser extension for pages acting as bad boys. NB: This is the code repository of the project, if...
[sc name=”ad_1″] Spam is a common nuisance for users of the Internet. However, it is not just annoying – these messages may cause substantial harm...
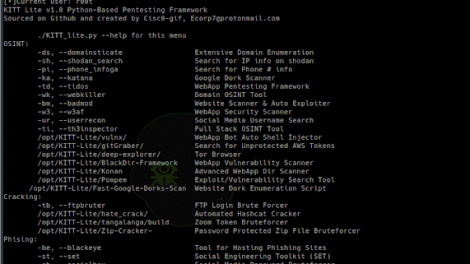
[sc name=”ad_1″] The KITT Penetration Testing Framework was developed as an open source solution for pentesters and programmers alike to compile the tools...
[sc name=”ad_1″] 2020-06-06 Update: this trick no longer works on the latest builds of Windows 10 Insider Preview. This means that, although it still works...
[sc name=”ad_1″] OpenVPN is open-source commercial software that implements virtual private network techniques to create secure point-to-point or site-to...
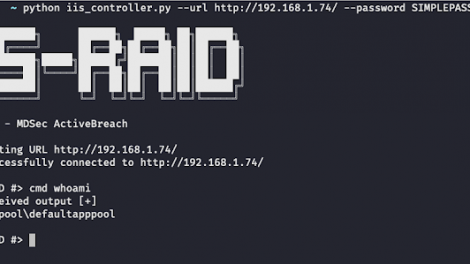
[sc name=”ad_1″] IS Raid is a native IIS module that abuses the extendibility of IIS to backdoor the web server and carry out custom actions defined by an...
[sc name=”ad_1″] Can a more complex comparison be made? AI and voice assistance are similar to a seeing-eye dog. Throwing the duties of a service dog into...
[sc name=”ad_1″] What is cross-site scripting (XSS)? Cross-site scripting (also known as XSS) is a web security vulnerability that allows an attacker to...
[sc name=”ad_1″] kube-bench is a Go application that checks whether Kubernetes is deployed securely by running the checks documented in the CIS Kubernetes...
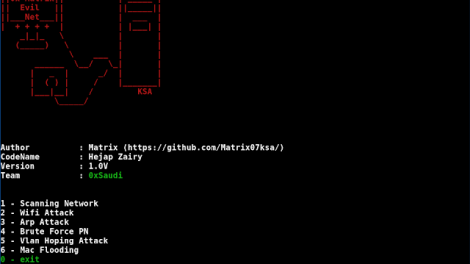
[sc name=”ad_1″] Network Attack wifi attack vlan attack arp attack Mac Attack Attack revealed etc../ install : sudo pip3 install -r requirements.txt EvilNet...