ACLight is a tool for discovering privileged accounts through advanced ACLs (Access Lists) analysis. It includes the discovery of Shadow Admins in the scanned network...
Programming Languages : BASH RUN root@ismailtasdelen:~# bash ./anti-ddos.sh Cloning an Existing Repository ( Clone with HTTPS ) git clone Cloning an Existing Repository...
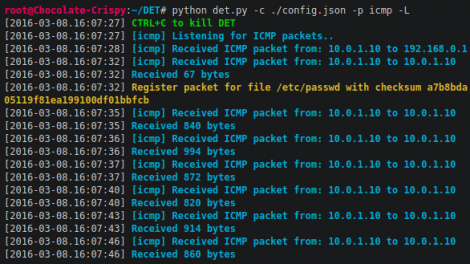
DET (is provided AS IS), is a proof of concept to perform Data Exfiltration using either single or multiple channel(s) at the same time. This is a Proof of Concept aimed...
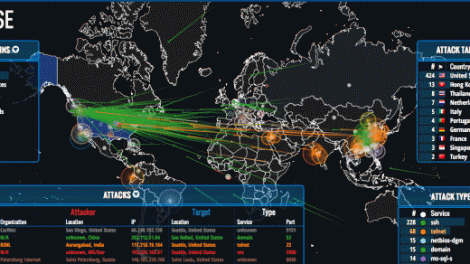
The Bitcoin rose by higher than 8% to $5,243 having begun the year at $966. Bitcoin has risen by more than 750% in the past year and is meriting four times as much as an...
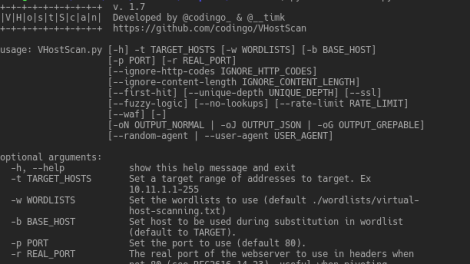
A virtual host scanner that can be used with pivot tools, detect catch-all scenarios, aliases and dynamic default pages. First presented at SecTalks BNE in September...
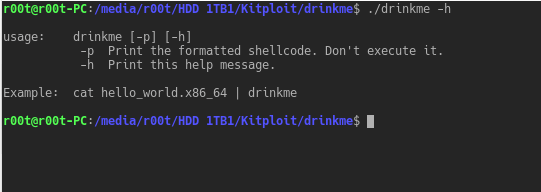
drinkme is a shellcode test harness. It reads shellcode from stdin and executes it. This allows pentesters to quickly test their payloads before deployment. Formats...
What if I told you that there is a method will let you execute commands on Microsoft Word without any Macros, or memory corruption?! This Macro-less code execution in...
Security researchers from AccessNow have discovered a new Facebook phishing scam that can also fool a professional technical user into falling victim to this scam and...
Reverse Engineer .NET Assemblies dnSpy is a tool to reverse engineer .NET assemblies. It includes a decompiler, a debugger and an assembly editor (and more) and can be...
The project is designed as a file resource cloner. Metadata, including digital signature, is extracted from one file and injected into another. Note: The signature is...