Taking advantage of Intel ME technology, within which attackers can execute unsigned code on the target machine. This leads to a full compromise of the platform. Intel...
Not the first news of this nature but it was very recently discovered that Microsoft suffered a cyber attack from a group of very intelligent hackers way back in 2013...
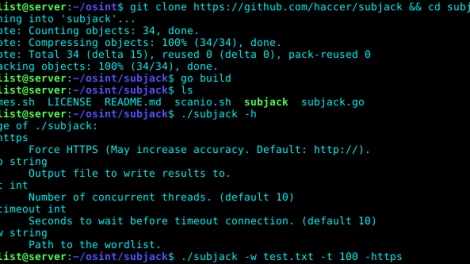
subjack is a Hostile Subdomain Takeover tool written in Go designed to scan a list of subdomains concurrently and identify ones that are able to be hijacked. With...
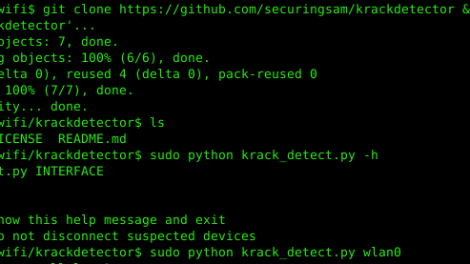
KRACK Detector is a Python script to detect possible KRACK attacks against client devices on your network. The script is meant to be run on the Access Point rather than...
Seccubus automates regular vulnerability scans with various tools and aids security people in the fast analysis of its output, both on the first scan and on repeated...
objection is a runtime mobile exploration toolkit, powered by Frida. It was built with the aim of helping assess mobile applications and their security posture without...
Many internet giants offer security measures like two-factor authentication (which you should really use) to keep your account safe from hackers. But there are a handful...
Studies on the topic of in-browser miners have been going on the Chromium project’s bug tracker since mid-September when Coinhive, the first launched. To experience...
Agari supports email fraud on behalf of larger than 400 federal websites, including the real sites of the departments of Health and Human Services and Veterans Affairs...
BaRMIe is a tool for enumerating and attacking Java RMI (Remote Method Invocation) services. RMI services often expose dangerous functionality without adequate security...