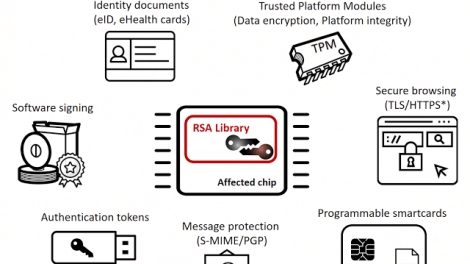
This tool is related to ACM CCS 2017 conference paper #124 Return of the Coppersmith’s Attack: Practical Factorization of Widely Used RSA Moduli. It enables you to test...
Another crop of Android apps hiding malware have been discovered in – and removed from – the Google Play store. Researchers at ESET discovered eight apps...
A series of recently disclosed critical Bluetooth flaws that affect billions of Android, iOS, Windows and Linux devices have now been discovered in millions of AI-based...
This hack was not conducted in a laboratory, but on a 757 gathered at the airport in Atlantic City, N.J. And the real hack happened over a year ago. We are only now...
Right now, while artificial intelligence is concentrating on profit-generation, natural knowledge has proven to be higher than up to the task of manipulating it, as if...
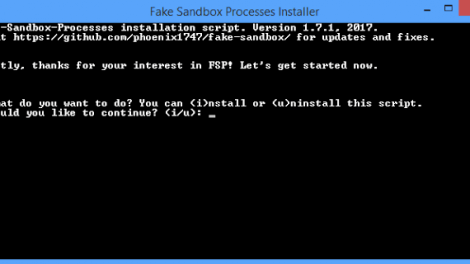
This small script will simulate fake processes of analysis, sandbox and/or VM software that some malware will try to avoid. You can download the original script (made by...
A CMS Exploit Framework. Requirements python2.7 Works on Linux, Windows Usage usage: cmspoc.py [-h] -t TYPE -s SCRIPT -u URL optional arguments: -h, --help show this...
Adobe’s latest security update has swatted a total of 67 bugs, some of them critical, in Adobe Flash, Acrobat, and Reader. On Tuesday, the software provider...
Forever 21 is investigating a potential data breach which may have compromised customer information and payment cards. On Tuesday, the US clothing retailer said that the...
The federal government on Tuesday issued an alert detailing the North Korean government’s use of malware known as FALLCHILL, warning that North Korea has likely...