The researchers demanded data left visible entered names, phone numbers, locations and Google queries. The chief of the Israeli company back the app confirmed the breach...
It’s the latest movement in a clash between Amazon and Google, which has seen the two businesses hold their products off the rival’s programs and services. It’s not the...
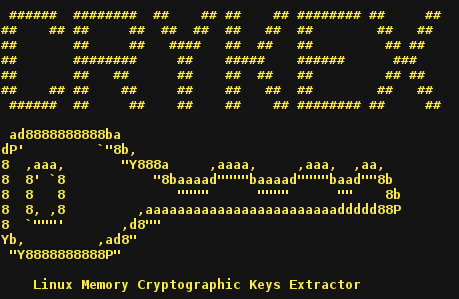
Some work has been already published regarding the subject of cryptograhic keys security within DRAM. Basically, we need to find something that looks like a key...
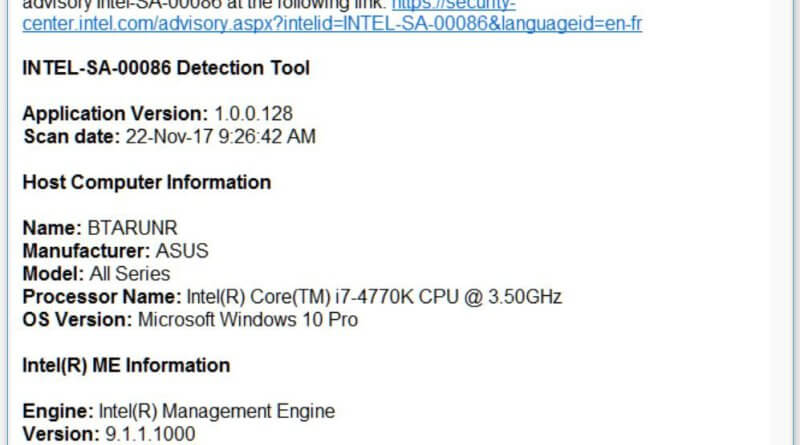
These ME security holes affect millions of computers. ME continues Intel’s Active Management Technology (AMT). This is a great tool that allows admins to remotely run...
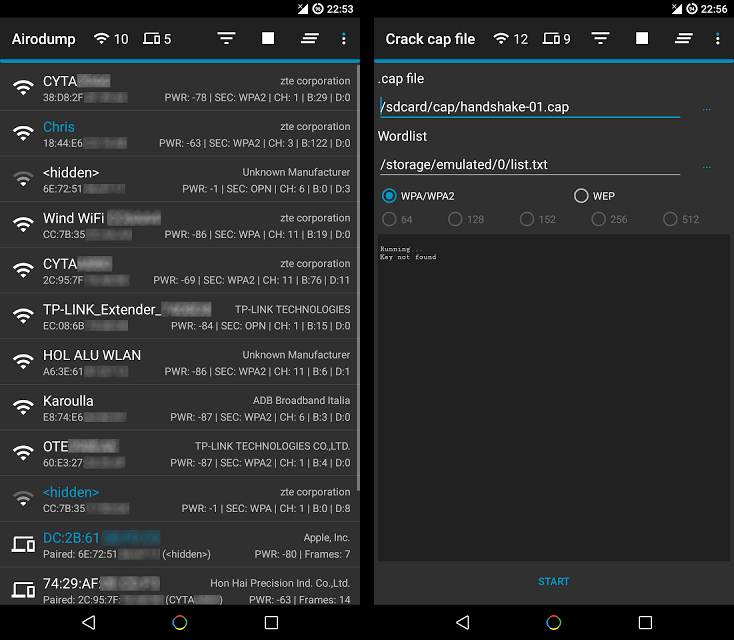
Hijacker is a Graphical User Interface for the penetration testing tools Aircrack-ng, Airodump-ng, MDK3 and Reaver. It offers a simple and easy UI to use these tools...
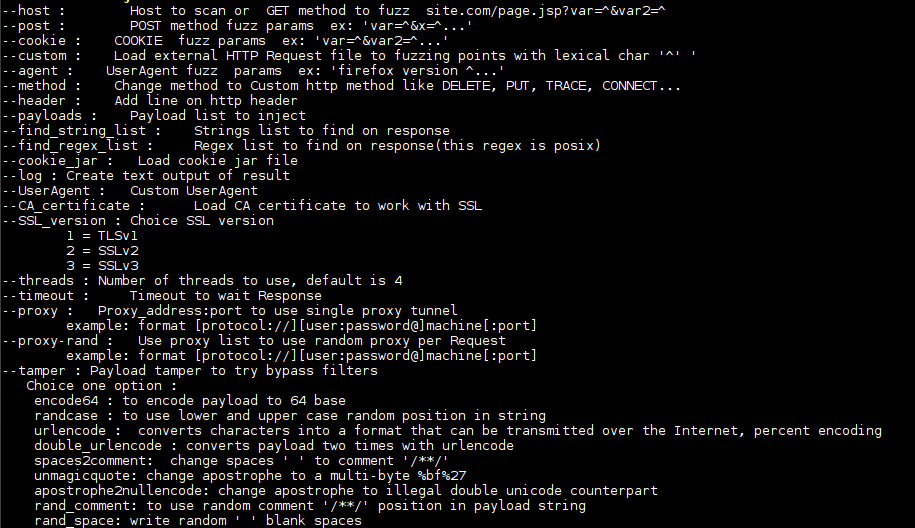
Web security tool to make fuzzing at HTTP inputs, made in C with libCurl. 0d1n is a tool for automating customized attacks against web applications. You can do: Brute...
ratched is a Man-in-the-Middle (MitM) proxy that specifically intercepts TLS connections. It is intended to be used in conjunction with the Linux iptables REDIRECT...
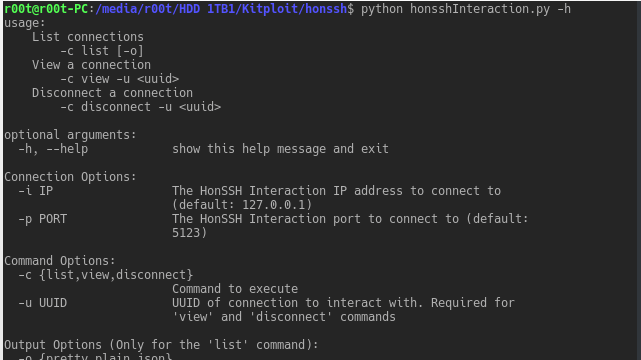
HonSSH is a high-interaction Honey Pot solution. HonSSH will sit between an attacker and a honey pot, creating two separate SSH connections between them. Features...
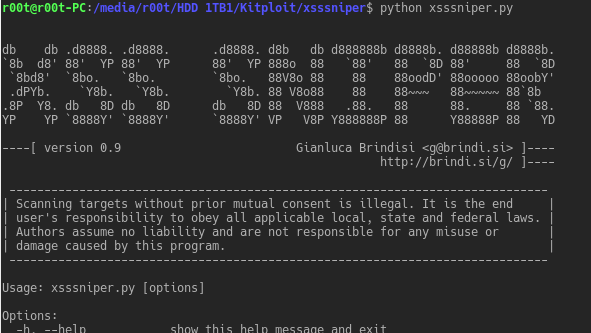
XSSSNIPER is an handy xss discovery tool with mass scanning functionalities. Usage: Usage: xsssniper.py [options] Options: -h, --help show this help message and exit -u...
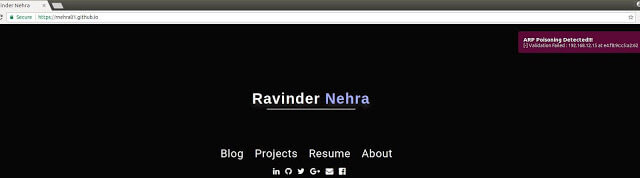
Security Tool to detect arp poisoning attacks. Features Uses a faster approach in detection of arp poisoning attacks compared to passive approaches Detects not only...