- First start a VM (see warning above) if you are going to be unpacking malware.
- Install Python 2.7
- Remember to set your python and pip paths ; )
- Install Frida by typing
pip install fridain cmd - Clone this repository and you are ready to extract!
- CreateProcess
- WriteVirtualMemory (to remote process)
- ResumeThread (in remote process)
- CreateProcess
- NtCreateSection
- NtUnmapViewOfSection (remote process)
- NtMapViewOfSection (remote process)
Examples
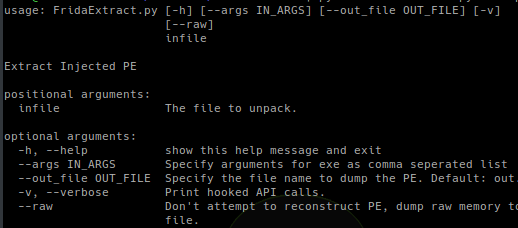
By default FridaExtract will attempt to automatically extract the injected PE file, reconstruct it, and dump it to a file called dump.bin.
python FridaExtract.py bad.exeDump To File
A dump file can be specified using the --out_file command.
python FridaExtract.py bad.exe --out_file extracted.exePass Arguments
If the packed PE file you are attempting to extract requires arguments you can pass them using the --args command. Multiple arguments can be passed as comma separated.
python FridaExtract.py bad.exe --args passwordDump Raw
FridaExtract will automatically attempt to reconstruct the dumped memory into a PE file. If this isn’t working and you just want a raw dump of all memory written to the subprocess you can use the --raw command. Instead of writing the reconstructed PE to the dump file the raw memory segments will be written in order of address.
python FridaExtract.py bad.exe --rawVerbose
FridaExtract uses hooks on the following APIs to extract the injected PE file:
- ExitProcess
- NtWriteVirtualMemory
- NtCreateThread
- NtResumeThread
- NtDelayExecution
- CreateProcessInternalW
- NtMapViewOfSection
- NtUnmapViewOfSection
- NtCreateSection
To trace these APIs and print the results use the -v or --verbose command.
python FridaExtract.py bad.exe --verboseCaveats
Frida uses userland hooks that can easily be bypassed. If you need a more robust DBI tool try PIN! A great example of using PIN to extract RunPE is provided by here.
Frida injects a javascript runtime into the process you are analyzing, it is not stealthy. For a decent overview of how Frida may be detected by malware check this out.
Acknowledgments
- Huge thanks to @oleavr for helping me with my endless questions about Frida
- Hat tip to @skier_t for his awesome PE rebuilding script and so much more!
Feedback / Help
- Any questions, comments, requests hit us up on twitter: @herrcore or @seanmw
- Anything Frida specific find us lurking on IRC: #frida at irc.freenode.net
- Pull requests welcome!


















Add Comment