An OSINT tool to find contacts in order to report security vulnerabilities.
Installation
Linux
Make sure you have installed the whois and jq packages.
$ git clone https://github.com/EdOverflow/contact.sh.git
$ cd contact.sh/
$ chmod u+x contact.sh
$ ./contact.sh -d google.com -c googleOSX
$ brew install gnu-sed --with-default-names
$ brew install jq
$ git clone https://github.com/EdOverflow/contact.sh.git
$ cd contact.sh/
$ chmod u+x contact.sh
$ ./contact.sh -d google.com -c googleUsage
$ ./contact.sh
_ _ __ _|_ _ _ _|_ _ |_
(_ (_)| | |_(_|(_ |_ o _> | |
---
by EdOverflow
[i] Description: An OSINT tool to find contacts in order to report security vulnerabilities.
[i] Usage: ./contact.sh [Options] use -d for hostnames (-d example.com), -c for vendor name (-c example), and -f for a list of hostnames in a file (-f domains.txt)
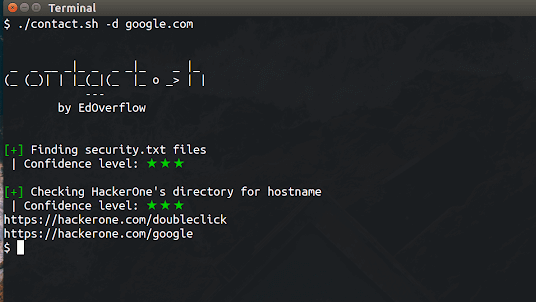
[i] Example: ./contact.sh -d google.com -c googleUse the -d flag when trying to find addresses linked to a domain. contact.sh will return a “Confidence level” based on the source of the information retrieved. A security.txt file located on the domain will have a higher priority than a Twitter account on the company’s website.
$ ./contact.sh -d google.comThe -c flag allows you to specify the company’s name.
$ ./contact.sh -c googleIf the company’s name contains spaces, make sure to place the name inside quotes.
$ ./contact.sh -c "keeper security"You can check a list of domains using the -f flag.
$ ./contact.sh -f domains.txtFor the best results, combine both flags as follows:
$ ./contact.sh -d google.com -c googlecontact.sh abides by the target’s robots.txt file.
$ ./contact.sh -d linkedin.com
_ _ __ _|_ _ _ _|_ _ |_
(_ (_)| | |_(_|(_ |_ o _> | |
---
by EdOverflow
[+] Finding security.txt files
| Confidence level: ★ ★ ★
[!] The robots.txt file does not permit crawling this hostname.
[+] Checking HackerOne's directory for hostname
| Confidence level: ★ ★ ★
https://hackerone.com/linkedin


















Add Comment