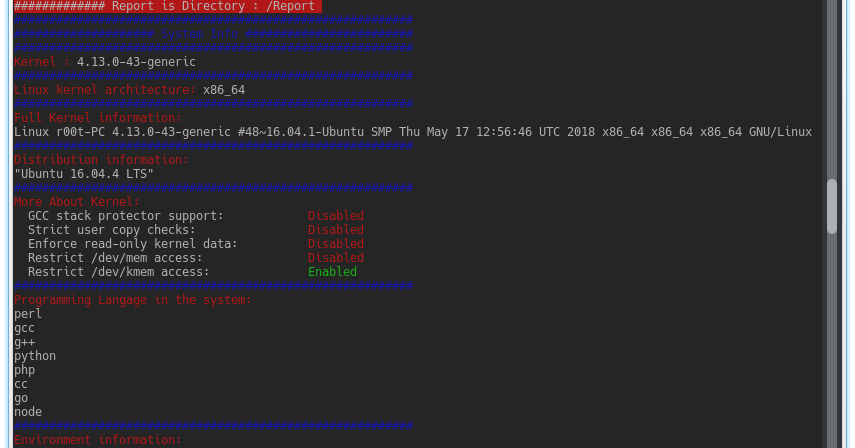
New Linux Privilege Escalation Tool. Getting Started System Information Gatherer Kernel Information Gatherer Checking Development environments on the system...
Category - Post Exploitation
The purpose of the Post-Exploitation phase is to determine the value of the machine compromised and to maintain control of the machine for later use. The value of the machine is determined by the sensitivity of the data stored on it and the machines usefulness in further compromising the network.
Magic Unicorn is a simple tool for using a PowerShell downgrade attack and inject shellcode straight into memory. Based on Matthew Graeber’s powershell attacks...
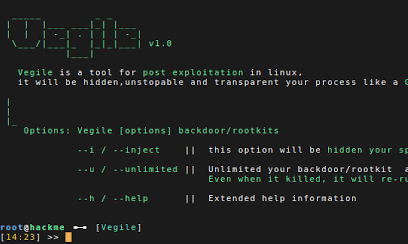
Vegile is a tool for Post exploitation Techniques in linux. Post Exploitation techniques will ensure that we maintain some level of access and can...
DNSExfiltrator allows for transfering (exfiltrate) a file over a DNS request covert channel. This is basically a data leak testing tool allowing to exfiltrate...
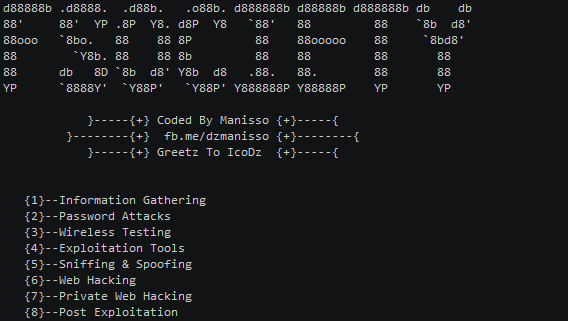
A Penetration Testing Framework , you will have every script that a hacker needs Menu Information Gathering Password Attacks Wireless Testing Exploitation...
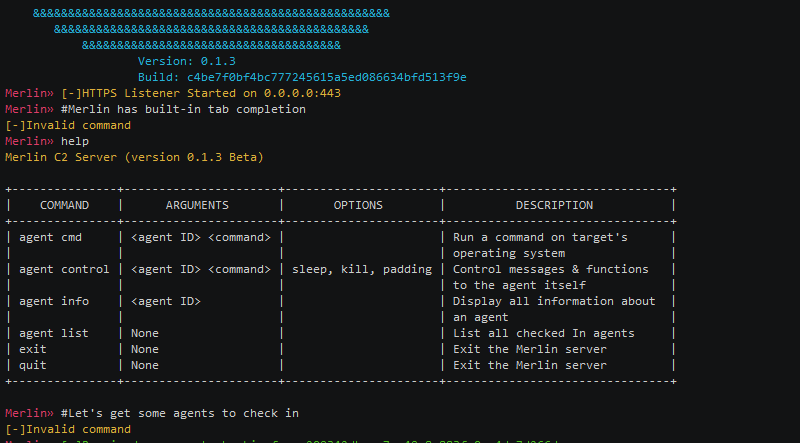
Merlin is a cross-platform post-exploitation framework that leverages HTTP/2 communications to evade inspection. HTTP/2 is a relatively new protocol that...
DBC2 (DropboxC2) is a modular post-exploitation tool, composed of an agent running on the victim’s machine, a controler, running on any machine...
Nishang is an open source framework and collection of powerful PowerShell scripts and payloads that you can use during penetration testing audit, post...
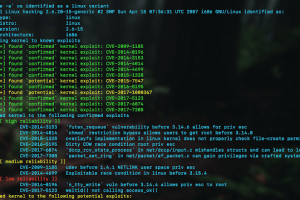
kernelpop is a framework for performing automated kernel exploit enumeration on Linux, Mac, and Windows hosts. Requirements python3 Currently supported...
Portia aims to automate a number of techniques commonly performed on internal network penetration tests after a low privileged account has been compromised...