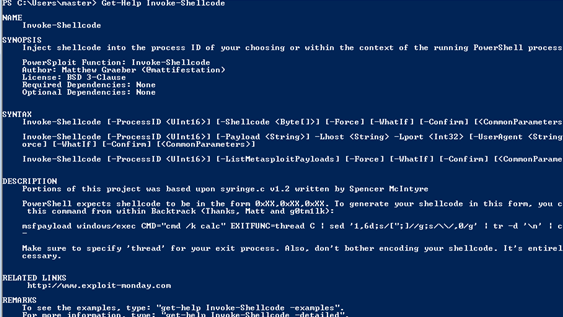
[sc name=”ad_1″] PowerSploit is a collection of Microsoft PowerShell modules that can be used to aid penetration testers during all phases of an...
Category - Post Exploitation
The purpose of the Post-Exploitation phase is to determine the value of the machine compromised and to maintain control of the machine for later use. The value of the machine is determined by the sensitivity of the data stored on it and the machines usefulness in further compromising the network.
[sc name=”ad_1″] Here you will find privilege escalation tools for Windows and Linux/Unix* (in some near future also for Mac). These tools search...
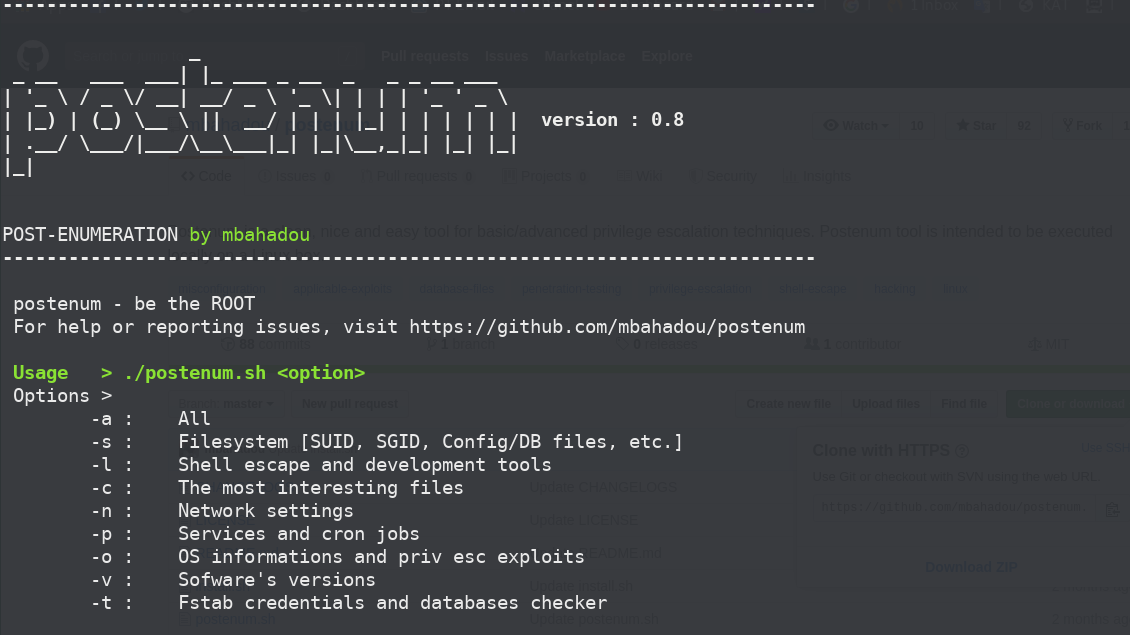
[sc name=”ad_1″] Postenum is a clean, nice and easy tool for basic/advanced privilege escalation vectors/techniques. Postenum tool is intended to...
[sc name=”ad_1″] Lockdoor Framework : A Penetration Testing Framework With Cyber Security Resources. 09/2019 : 1.0Beta Information Gathring Tools...
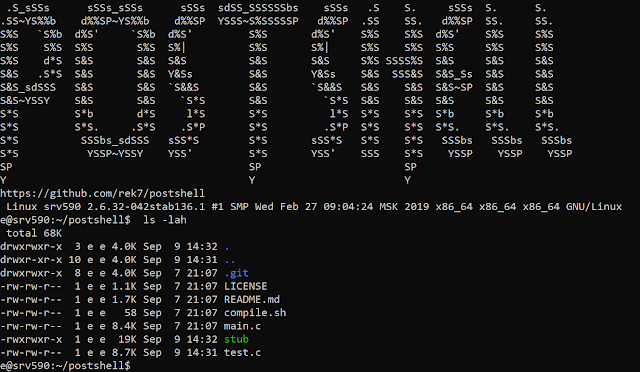
[sc name=”ad_1″] PostShell is a post-exploitation shell that includes both a bind and a back connect shell. It creates a fully interactive TTY...
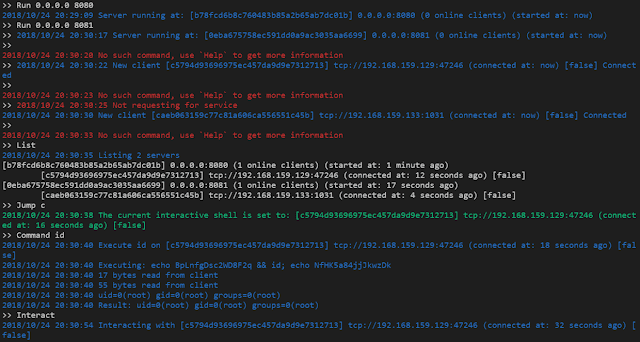
[sc name=”ad_1″] A modern multiple reverse shell sessions/clients manager via terminal written in go. Features Multiple service listening port...
Tested on Kali Linux. Should work with all Debian based distros (and other ones if you have the right packages installed) BabySploit is a penetration testing...
A post-exploitation agent powered by Python, IronPython, C#/.NET. Requirements Server requires Python >= 3.7 SILENTTRINITY C# implant requires .NET >= 4...
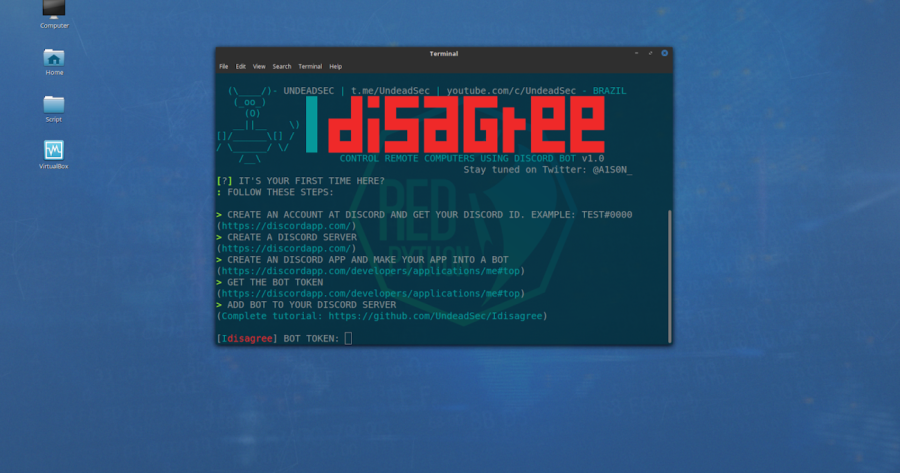
Control remote computers using discord bot and python 3. [ ! ] If your target is a windows system, you may want to compile your payload. Do this with py2exe or...
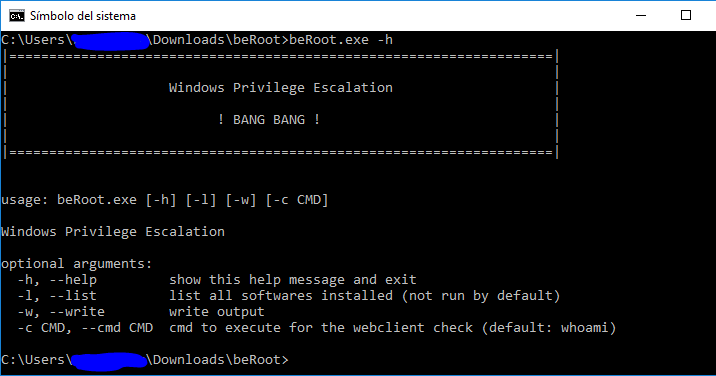
BeRoot(s) is a post exploitation tool to check common Windows misconfigurations to find a way to escalate our privilege. A compiled version is available here...