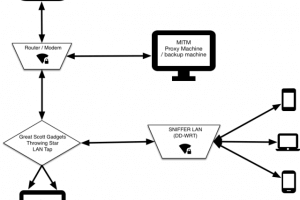
Essentially it’s a WiFi hotspot that is continually collecting all the packets transmitted across it. All connected clients’ HTTPS communications are subjected...
Category - Man-In-The-Middle
Man-In-The-Middle attack (MITM) is an attack where the attacker secretly relays and possibly alters the communication between two parties who believe they are directly communicating with each other.
Easily launch a new phishing site fully presented with SSL and capture credentials along with 2FA tokens using CredSniper. The API provides secure access to...
A robust Phishing Framework with a full featured CLI interface. The project was born out necessity through of years of engagements with tools that just didn’t...
pythem is a multi-purpose pentest framework written in Python. It has been developed to be used by security researchers and security professionals. The tool...
A python program to create a fake AP and sniff data new in 2.0: SSLstrip2 for HSTS bypass Image capture with Driftnet TShark for command line .pcap capture...
Xerosploit is a penetration testing toolkit whose goal is to perform man in the middle attacks for penetration testing purposes. It brings various modules...
Sniffer is a C program that parses and interprets captured Ethernet traffic containing IP datagrams (UDP/TCP), and stores the captured payloads, email messages...
Attack vectors There are 4 attack vectors available: beacon creds meterpreter meterpreter-grant For the ‘creds’ method, macphish can generate the Applescript...
bettercap is a complete, modular, portable and easily extensible MITM tool and framework with every kind of diagnostic and offensive feature you could need in...