[sc name=”ad_1″] Tested environments: Windows, MAC, linux, and windows subsystem for linux (WSL) What can SourceWolf do? Crawl through responses to...
Category - Information Gathering
Information gathering is the most time-consuming and laborious phase of the attack cycle but is often a major determinant of the success or failure of the engagement.
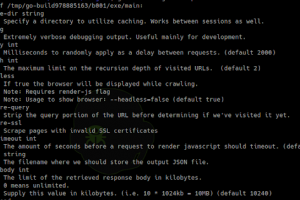
[sc name=”ad_1″] A golang utility to spider through a website searching for additional links with support for JavaScript rendering. Install go get ...
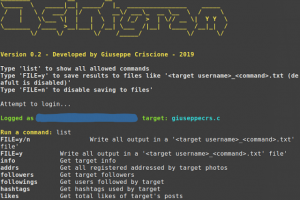
[sc name=”ad_1″] Osintgram is a OSINT tool on Instagram. Osintgram offers an interactive shell to perform analysis on Instagram account of any...
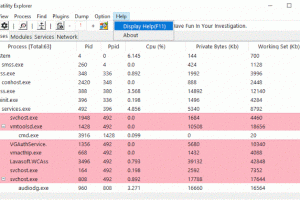
[sc name=”ad_1″] This program allows the user to access a Memory Dump. It can also function as a plugin to the Volatility Framework (). This...
[sc name=”ad_1″] Yeti is a platform meant to organize observables, indicators of compromise, TTPs, and knowledge on threats in a single, unified...
[sc name=”ad_1″] Automatically scan for publically accessible webcams around the internet Usage python MJPG.py : for public MJPG streamers around...
[sc name=”ad_1″] Do you want to get threat intelligence data about a file, an IP or a domain? Do you want to get this kind of data from multiple...
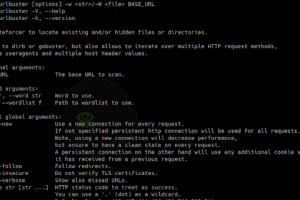
[sc name=”ad_1″] Powerful web directory fuzzer to locate existing and/or hidden files or directories. Similar to dirb or gobuster, but with a lot...
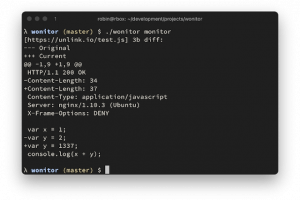
[sc name=”ad_1″] fast, zero config web endpoint change monitor. for comparing responses, a selected list of http headers and the full response body...
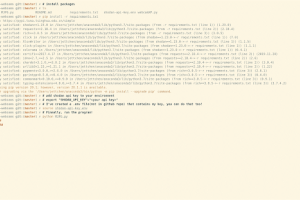
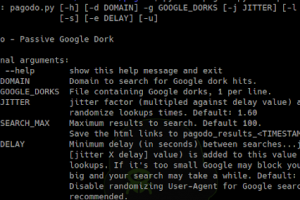
[sc name=”ad_1″] The goal of this project was to develop a passive Google dork script to collect potentially vulnerable web pages and applications...