[sc name=”ad_1″] Chrome extension for Instant access to your bug bounty submission dashboard of various platforms + publicly disclosed reports +...
Category - Information Gathering
Information gathering is the most time-consuming and laborious phase of the attack cycle but is often a major determinant of the success or failure of the engagement.
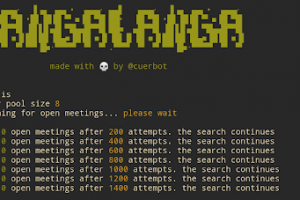
[sc name=”ad_1″] Zoom Conference scanner. This scanner will check for a random meeting id and return information if available. Usage This are all...
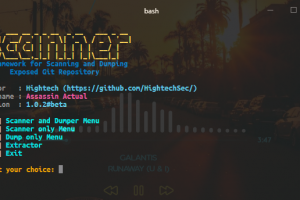
[sc name=”ad_1″] This tool can scan websites with open .git repositories for Bug Hunting/ Pentesting Purposes and can dump the content of the .git...
[sc name=”ad_1″] The script aims to help in classifying vulnerabilities in web applications. The methodology RecoX is arising can spot weaknesses...
[sc name=”ad_1″] GitMonitor is a Github scanning system to look for leaked sensitive information based on rules. I know that there are a lot of...
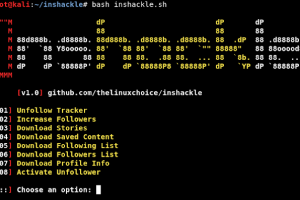
[sc name=”ad_1″] Instagram hacks: Track unfollowers, Increase your followers, Download Stories, etc Features: Unfollow Tracker Increase Followers...
[sc name=”ad_1″] Enumy is portable executable that you drop on target Linux machine during a pentest or CTF in the post exploitation phase. Running...
[sc name=”ad_1″] Bing-ip2hosts is a Bing.com web scraper to discover hostnames by IP address. Description Bing-ip2hosts is a Bing.com web scraper...
[sc name=”ad_1″] ADCollector is a lightweight tool that enumerates the Active Directory environment to identify possible attack vectors. It will...
[sc name=”ad_1″] All-in-one tool for managing vulnerability reports Why The goal of Purify to be an easy-in-use and efficient tool to simplify a...