[sc name=”ad_1″] Perform automated network reconnaissance scans to gather network intelligence. IntelSpy is a multi-threaded network intelligence...
Category - Exploitation Tools
Web Services Scanning that are frequently used by companies since communication between network, application and web based devices are improved. Its also used to report vulnerabilities with a high degree of accuracy and specificity and with this tool, you can actively exploit vulnerabilities.
[sc name=”ad_1″] Yet another PoC for Blogpost: To be used with a cmd that does whatever the F you want, for a dll that pops cmd, . check the list...
[sc name=”ad_1″] A polyglot payload generator Introduction SNOWCRASH creates a script that can be launched on both Linux and Windows machines...
[sc name=”ad_1″] Quiver is the tool to manage all of your tools. It’s an opinionated and curated collection of commands, notes and scripts...
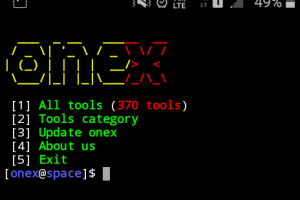
[sc name=”ad_1″] “onex a hacking tools library.” Onex is a kali linux hacking tools installer for termux and other linux distribution...
[sc name=”ad_1″] A graphical interface to use information security tools by the browser. Getting Started Kali Linux Tools Interface is a graphical...
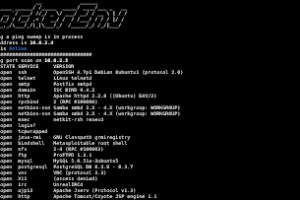
[sc name=”ad_1″] hackerEnv is an automation tool that quickly and easily sweep IPs and scan ports, vulnerabilities and exploit them. Then, it hands...
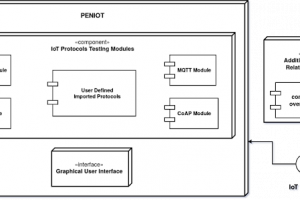
[sc name=”ad_1″] PENIOT is a penetration testing tool for Internet of Things (IoT) devices. It helps you to test/penetrate your devices by...
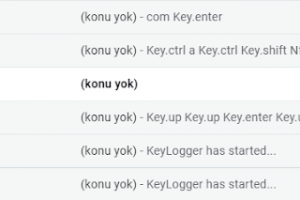
[sc name=”ad_1″] Inputs To Mail. Get Keyboard,Mouse,ScreenShot,Microphone Inputs and Send to your Mail. Purpose of the project is testing the...
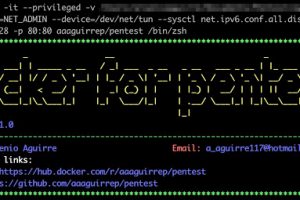
[sc name=”ad_1″] Docker for pentest is an image with the more used tools to create an pentest environment easily and quickly. Features OS...