Linux ELF x32 and x64 ASLR bypass exploit with stack-spraying. Properties: ASLR bypass Cross-platform Minimalistic Simplicity Unpatchable Dependencies: Linux 2...
Category - Exploitation Tools
Web Services Scanning that are frequently used by companies since communication between network, application and web based devices are improved. Its also used to report vulnerabilities with a high degree of accuracy and specificity and with this tool, you can actively exploit vulnerabilities.
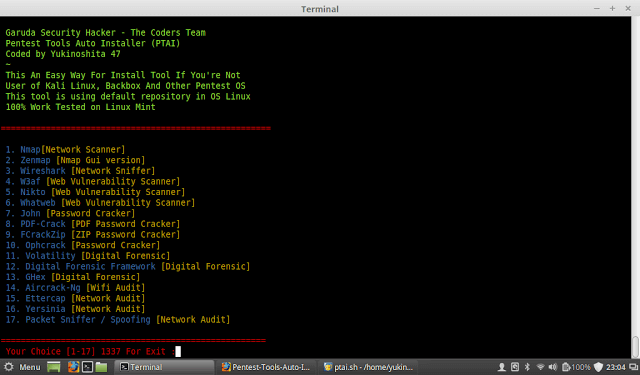
A Simple tool for installing pentest tools and forensic tools on Debian / Ubuntu Based OS Tested on Linux Mint And Kali Linux How To Do ?? Change Your...
Legal Disclaimer: This project is made for educational and ethical testing purposes only。It is the end user’s responsibility to obey all applicable local...
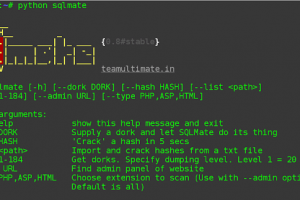
There are some features that we think SQLMap should have. Like finding admin panel of the target, better hash cracking etc. If you think the same, SQLMate is...
A script written lazily for generating reverse shell backdoors on the go whenever you need without any hassle for your daily penetration needs . These...
Reptile is a LKM rootkit for evil purposes. If you are searching stuff only for study purposes, see the demonstration codes. Features Give root to unprivileged...
The OWASP Zed Attack Proxy (ZAP) is one of the world’s most popular free security tools and is actively maintained by hundreds of international volunteers*. It...
Exploit Pack has been designed by an experienced team of software developers and exploit writers to automate processes so penetration testers can focus on...
A wrapper tool for shadowsocks to consistently bypass firewalls. Quick start Automatically connect The easiest way to run this tool is just type ssct in...
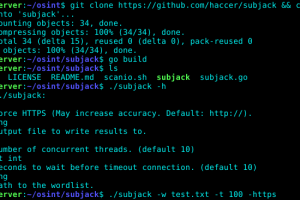
subjack is a Hostile Subdomain Takeover tool written in Go designed to scan a list of subdomains concurrently and identify ones that are able to be hijacked...