Defeating Google’s audio reCaptcha system with 85% accuracy. Inspiration Across the Internet, hundreds of thousands of sites rely on Google’s...
Category - Exploitation Tools
Web Services Scanning that are frequently used by companies since communication between network, application and web based devices are improved. Its also used to report vulnerabilities with a high degree of accuracy and specificity and with this tool, you can actively exploit vulnerabilities.
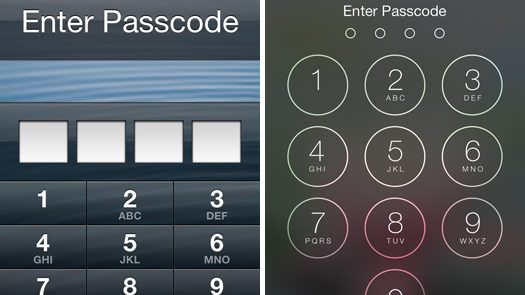
This version of the application is written with Python programming language,which is used to crack the Restriction PassCode of iphone/ipad. Brute Force Get the...
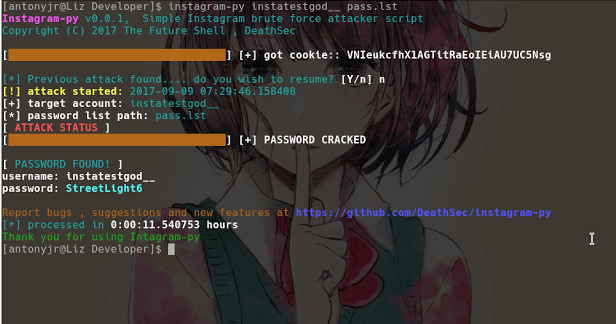
Instagram-Py is a simple python script to perform basic brute force attack against Instagram , this script can bypass login limiting on wrong passwords , so...
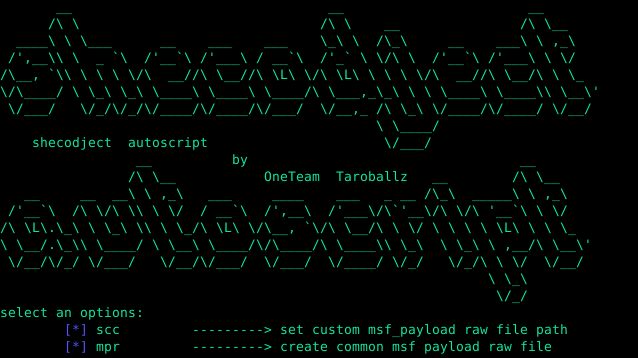
shecoject is a tool written in python3, which can be used to package raw metasploit-generated raw files directly into the pyinstaller package or you can use...
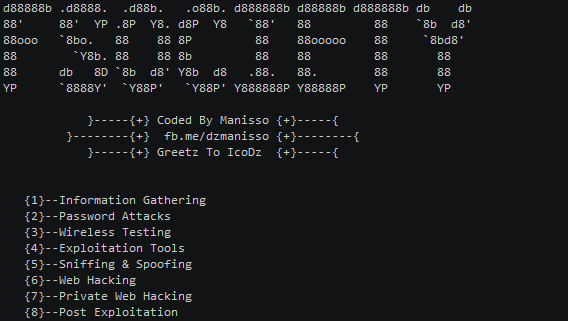
A Penetration Testing Framework , you will have every script that a hacker needs Menu Information Gathering Password Attacks Wireless Testing Exploitation...
Relayer is an SMB relay Attack Script that automates all the necessary steps to scan for systems with SMB signing disabled and relaying authentication request...
Tools for generating usernames when penetration testing. Usernames are half the password brute force problem. This is useful for user account/password brute...
BruteSpray takes nmap GNMAP/XML output and automatically brute-forces services with default credentials using Medusa. BruteSpray can even find non-standard...
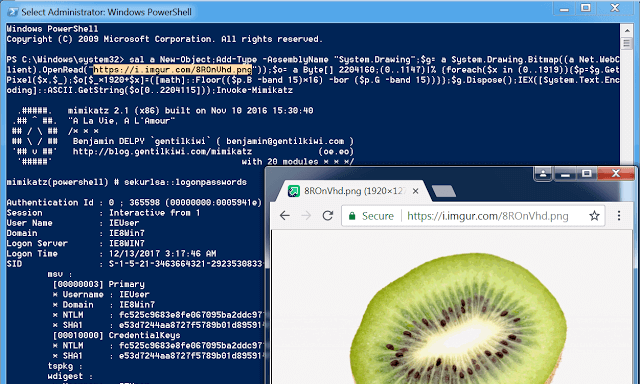
Invoke-PSImage takes a PowerShell script and embeds the bytes of the script into the pixels of a PNG image. It generates a oneliner for executing either from a...
XAttacker is a Website Vulnerability Scanner & Auto Exploiter developed by Mohamed Riahi Auto Cms Detect [1] WordPress : [+] Adblock Blocker [+] WP All...