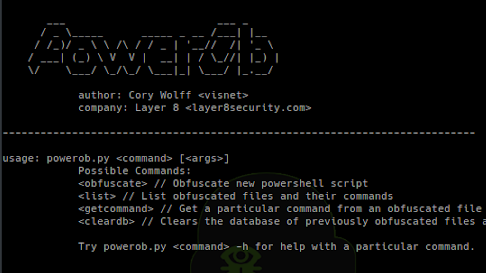
[sc name=”ad_1″] An on-the-fly Powershell script obfuscator meant for red team engagements. Built out of necessity. Installation git clone Usage...
Category - Exploitation Tools
Web Services Scanning that are frequently used by companies since communication between network, application and web based devices are improved. Its also used to report vulnerabilities with a high degree of accuracy and specificity and with this tool, you can actively exploit vulnerabilities.
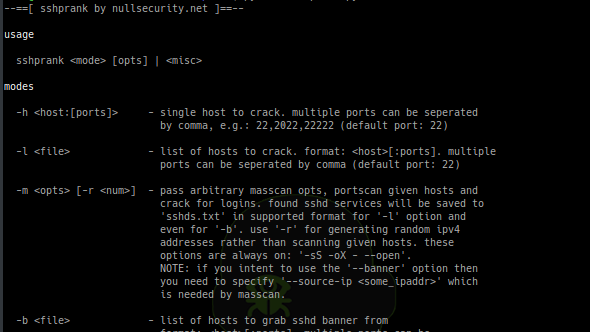
[sc name=”ad_1″] A fast SSH mass-scanner, login cracker and banner grabber tool using the python-masscan module. Usage [ hacker@blackarch ~ ]$...
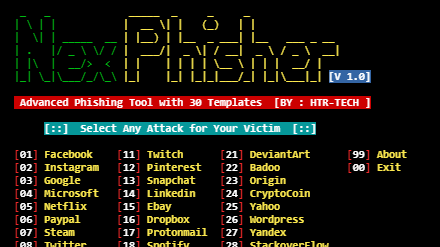
[sc name=”ad_1″] NexPhisher is an automated Phishing tool made for Termux & Linux .The phishing Pages are Taken from Zphisher under GNU General...
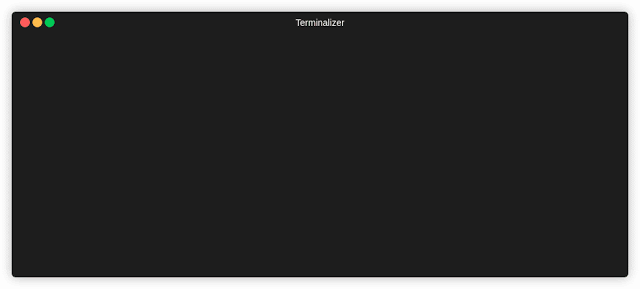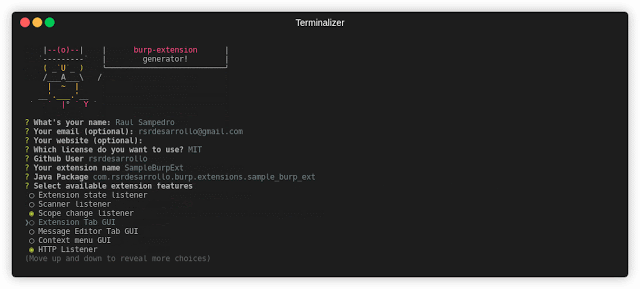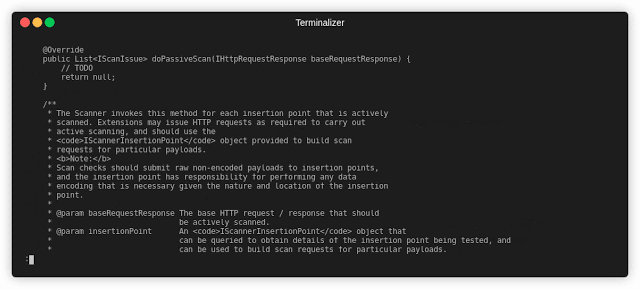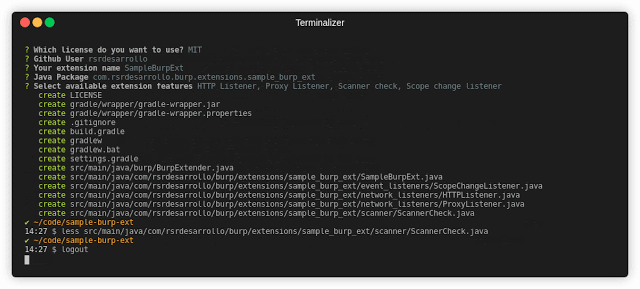
[sc name=”ad_1″] Everything You Need About Burp Extension Generation Installation First, install Yeoman and generator-burp-extension using npm (we...
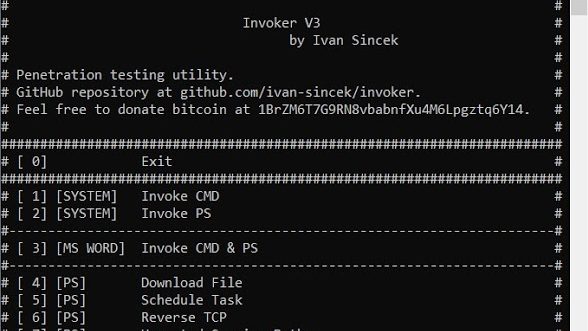
[sc name=”ad_1″] Penetration testing utility. The goal is to use this tool when access to some Windows OS features through GUI is restricted. Some...
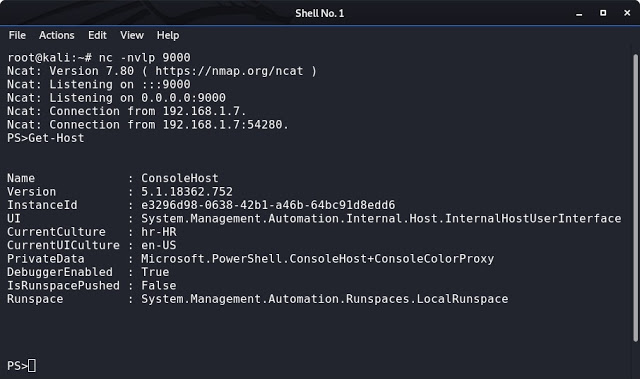
[sc name=”ad_1″] PowerShell script for connecting to a remote host. Remote host will have full control over client’s PowerShell and all its...
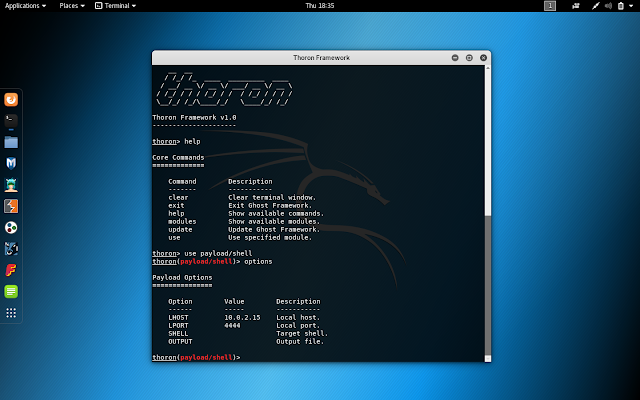
[sc name=”ad_1″] About Thoron Framework Thoron Framework is a Linux post-exploitation framework that exploit Linux tcp vulnerability to get shell...
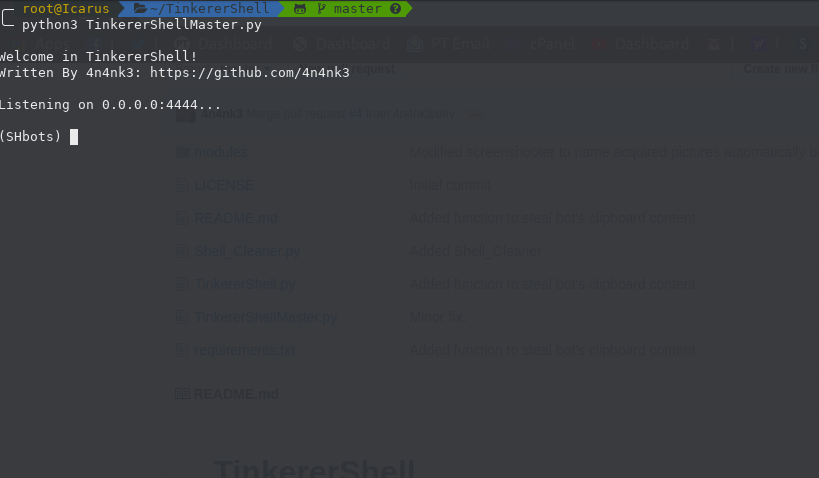
[sc name=”ad_1″]A simple reverse shell written in python 3.7 just for fun. Actually it supports Windows and Linux OS and integrates some basic...
[sc name=”ad_1″] snare – Super Next generation Advanced Reactive honEypot Super Next generation Advanced Reactive honEypot About SNARE is a...
[sc name=”ad_1″] UAC-A-Mola is a tool that allows security researchers to investigate new UAC bypasses, in addition to detecting and exploiting...