Shadow is a unique discrete-event network simulator that runs real applications like Tor and Bitcoin, and distributed systems of thousands of nodes on a single...
Author - Mazen Elzanaty
Multi-platform transparent client-side encryption of your files in the cloud. Cryptomator provides transparent, client-side encryption for your cloud. Protect...
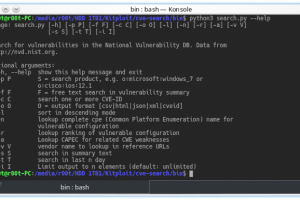
cve-search is a tool to import CVE (Common Vulnerabilities and Exposures) and CPE (Common Platform Enumeration) into a MongoDB to facilitate search and...
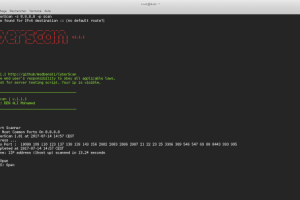
CyberScan is an open source penetration testing tool that can analyse packets , decoding , scanning ports, pinging and geolocation of an IP including...
This has been a story drifting around the internet the last few days. The victim was Elitoohey.He refined on the situation in a Reddit post, saying the bank...
Security researchers have discovered a new privilege-escalation vulnerability in Linux kernel that could allow a local attacker to execute code on the affected...
To comply with the law, the DPA states that Microsoft requires getting valid user consent this indicates the company must be open about what data is gathered...
About Getting default credentials added to commercial scanners is often difficult and slow. changeme is designed to be simple to add new credentials without...
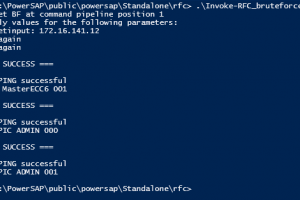
PowerSAP is a simple powershell re-implementation of popular & effective techniques of all public tools such as Bizploit, Metasploit auxiliary modules, or...
A convention in Athens, Greece, Munro detailed some of the appalling security lapses Pen Test Partners found while investigating naval ships that had things...