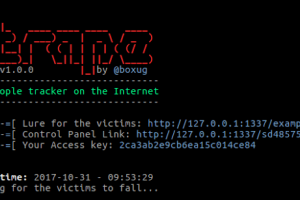
Trape is a recognition tool that allows you to track people, the information you can get is very detailed. We want to teach the world through this, as large...
Author - Mazen Elzanaty
A rogue Twitter employee deactivated President Trump’s personal Twitter account (@realdonaldtrump) on his last day as a customer support rep for the social...
Apple’s privacy signs do not spread to the thousands of app developers who will gain access to facial data in order to increase entertainment features for...
Cybercriminals decided to use the Search Engine Optimization (SEO) to make their malicious links more widespread in the search results, allowing them to gain...
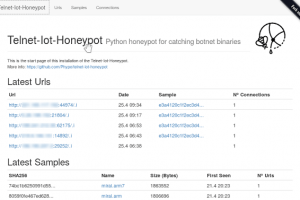
This project implements a python telnet server trying to act as a honeypot for IoT Malware which spreads over horribly insecure default passwords on telnet...
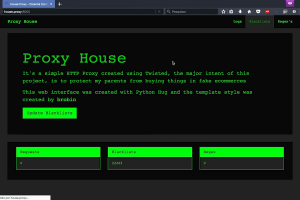
Protect your parents from phishing, HTTP proxy focused on block phishing URL’s Install git clone cd HouseProxy/ pip install -r requeriments.txt Config...
In 2013, Hackers apparently gained access to the Trump Organization’s domain booking account and created at least 250 website subdomains that cybersecurity...
The CryptoShuffler malware has been discovered by security researchers from Kaspersky Lab, cybercriminals are using this malware to steal cryptocurrencies from...
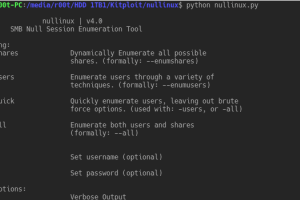
nullinux is an internal penetration testing tool for Linux that can be used to enumerate OS information, domain information, shares, directories, and users...
The cryptocurrency has had a bullish streak completely the week following the CME’s statement that it will introduce bitcoin expectations contracts. According...